Controlling inbound and outbound mail messages is a big challenge for sysadmins. Malware can spread quickly, infecting dozens of mailboxes and relentless spammers send thousands of messages with unsolicited advertising and phishing scams.
This article will show you how to prevent viruses, spam and malware by configuring a FreeBSD email gateway system using MailScanner, SpamAssassin, ClamAV and Postfix. The email gateway is responsible for analyzing, filtering, and cleaning or removing malicious files and messages (Figure 1). Figure 2 shows how the mail is scanned by the MailScanner. It is delivered to the incoming folder where it is analyzed by SpamAssassin and ClamAV and then delivered to the quarantine or queue folders. The cleaned messages are then delivered to the internal mail server.
Installing
Before you install the applications, it is necessary to update the FreeBSD ports tree to ensure you use the patched versions.
#cd /usr/ports
#portsnap fetch update
Installing Postfix MTA.
#cd /usr/ports/mail/postfix
#make install clean
#cd /usr/local/etc/postfix
#postalias aliases
Installing MailScanner.
#cd /usr/ports/mail/mailscanner
#make install clean
In the SpamAssassin options, uncheck the AS_ROOT for security reasons (Figure 4).
Configuring Postfix MTA
Configure Postfix by editing the /usr/local/etc/postfix/main.cf file (Listing 1), with some basic parameters described below:
• myhostname is the internet hostname of this mail system, use the FQDN;
• mydestination is the list of domains that are delivered via the mail delivery transport;
• mynetworks_style is the method used to generate the default value for the mynetworks parameter. The host value is when Postfix should “trust” only the local machine.
Create the transport_maps (Listing 2) to set the next hop; in our case, that is the internal mail server and header_checks (Listing 3) for content inspection of primary non-MIME message headers.
#cd /usr/local/etc/postfix
#vi transport
#portmap transport
#cd /usr/local/etc/postfix
#vi header_checks
The Sendmail is the default MTA in FreeBSD, so it is necessary to disable it and enable Postfix to start at boot (Listing 4).
Configuring MailScanner
Configure MailScanner by editing the /usr/local/etc/MailScanner/MailScanner.conf file, to manage the entire mail security system. Listing 5 shows the basic parameters necessary to configure it. The parameter Still Deliver Silent Viruses should not be used in a production environment, because the system will send thousands of MailScanner messages to the users. Improve MailScanner performance by increasing the Max Children parameter. Keep in mind each process consumes 20 MB. Create directory and configure necessary permissions.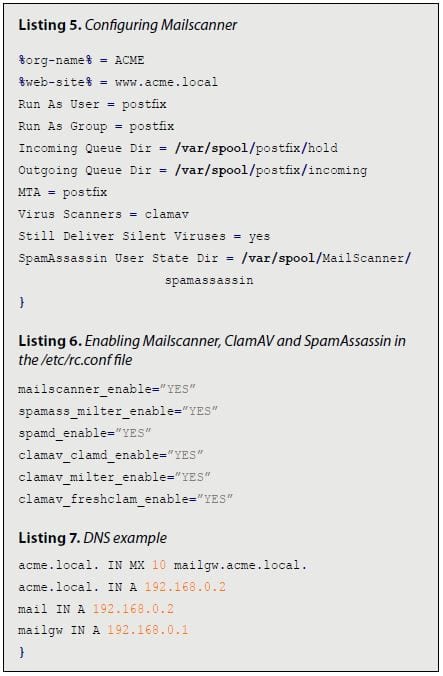
#mkdir -p /var/spool/Mailscanner/incoming && mkdir /var/ spool/Mailscanner/quarantine && mkdir /var/spool/Mailscanner/spamassassin
#chown -R postfix:postfix /var/spool/Mailscanner
#chmod -R 775 /var/spool/Mailscanner
Edit the /etc/rc.conf file to enable MailScanner, ClamAV and SpamAssassin to start at boot
Testing
To test your system, you need to configure the SMTP email client to use the email gateway. In my tests, I configured an MX record pointing to the email gateway (Listing 7) set in my client. I used the EICAR file to test the malware detection and system response. When sending an infected file, the system cleans the message, forwards it to the recipient (Figure 5) and alerts the sender (Figure 6).
Conclusion
The MailScanner is a very powerful security tool and one should test several configurations to best understand how it can help one’s mail service. MailScanner helps in the effective management of your mail security system that scales well in larger environments.
About the Author
Alexandro Silva aka Alexos lives in Salvador, Bahia, Brasil. He is an Information Security Consultant at iBliss Segurança & Inteligência. He has been using FreeBSD since the 4.11 release and can be reached on line at http://alexos.org.
This article was re-published with the permission of BSD Magazine. To Learn More about iXsystem’s commitment to open source check us out here: https://www.ixsystems.com/about-ix



