9. Sharing¶
Shares are created to make part or all of a volume accessible to other computers on the network. The type of share to create depends on factors like which operating systems are being used by computers on the network, security requirements, and expectations for network transfer speeds.
TrueNAS® provides a Wizard for creating shares. The Wizard automatically creates the correct type of dataset and permissions for the type of share, sets the default permissions for the share type, and starts the service needed by the share. It is recommended to use the Wizard to create shares, fine-tune the share settings using the instructions in the rest of this chapter if needed, then fine-tune the default permissions from the client operating system to meet the requirements of the network.
Note
Shares are created to provide and control access to an area of storage. Before creating shares, making a list of the users that need access to storage data, which operating systems these users are using, whether all users should have the same permissions to the stored data, and whether these users should authenticate before accessing the data is recommended. This information can help determine which type of shares are needed, whether multiple datasets are needed to divide the storage into areas with different access and permissions, and how complex it will be to set up those permission requirements. Note that shares are used to provide access to data. When a share is deleted, it removes access to data but does not delete the data itself.
These types of shares and services are available:
- AFP: Apple Filing Protocol shares are used when the client computers all run macOS. Apple has deprecated AFP in favor of SMB. Using AFP in modern networks is no longer recommended.
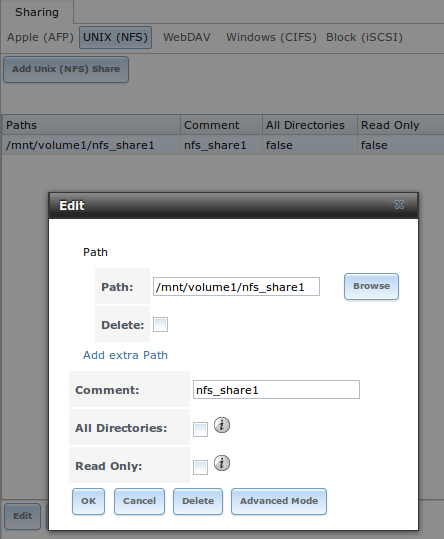
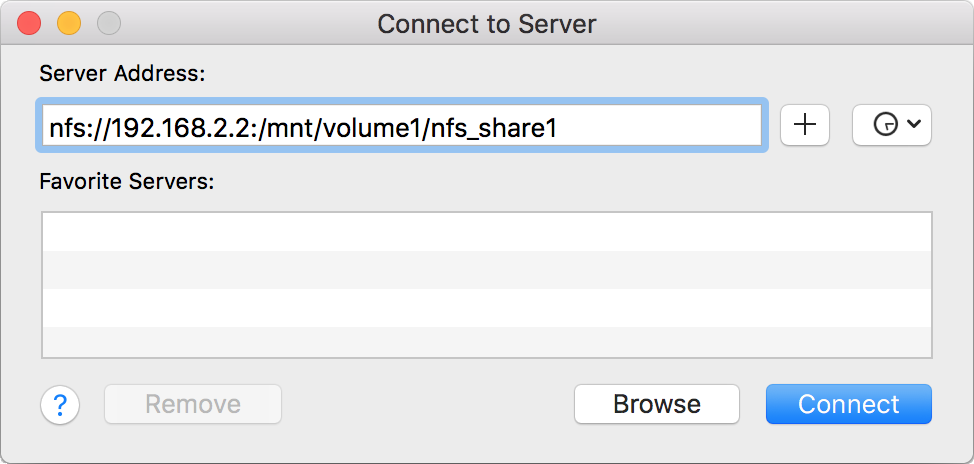
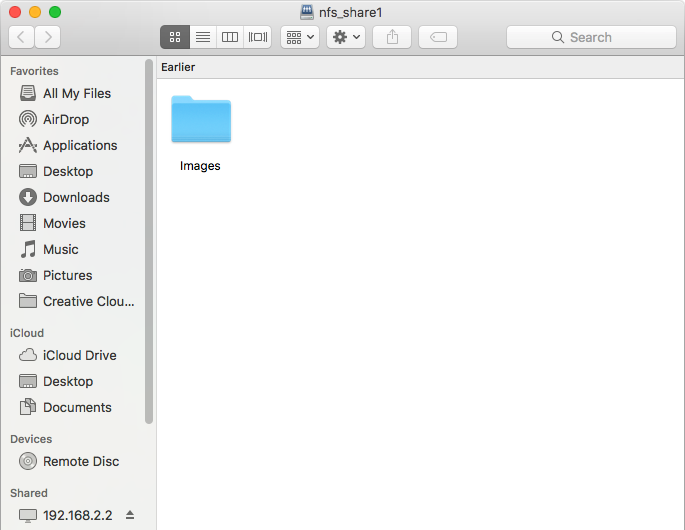
- Unix (NFS): Network File System shares are accessible from macOS, Linux, BSD, and the professional and enterprise versions (but not the home editions) of Windows. This can be a good choice when the client computers do not all run the same operating system but NFS client software is available for all of them.
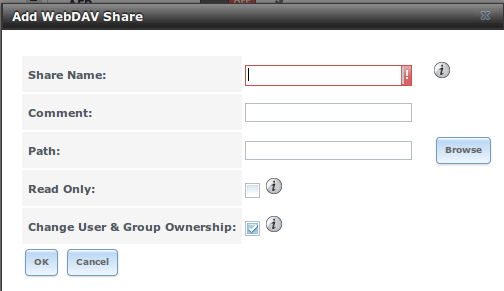
- WebDAV: WebDAV shares are accessible using an authenticated web browser (read-only) or WebDAV client running on any operating system.
- SMB: Server Message Block shares, also known as Common Internet File System (CIFS) shares, are accessible by Windows, macOS, Linux, and BSD computers. Access is slower than an NFS share due to the single-threaded design of Samba. SMB provides more configuration options than NFS and is a good choice on a network for Windows or Mac systems. However, it is a poor choice if the CPU on the TrueNAS® system is limited. If it is maxed out, upgrade the CPU or consider a different type of share.
- Block (iSCSI): block or iSCSI shares appear as an unformatted disk to clients running iSCSI initiator software or a virtualization solution such as VMware. These are usually used as virtual drives.
Fast access from any operating system can be obtained by configuring the FTP service instead of a share and using a cross-platform FTP file manager application such as Filezilla. Secure FTP can be configured if the data needs to be encrypted.
When data security is a concern and the network users are familiar with SSH command line utilities or WinSCP, consider using the SSH service instead of a share. It is slower than unencrypted FTP due to the encryption overhead, but the data passing through the network is encrypted.
Note
It is generally a mistake to share a volume or dataset with more than one share type or access method. Different types of shares and services use different file locking methods. For example, if the same volume is configured to use both NFS and FTP, NFS will lock a file for editing by an NFS user, but an FTP user can simultaneously edit or delete that file. This results in lost edits and confused users. Another example: if a volume is configured for both AFP and SMB, Windows users can be confused by the “extra” filenames used by Mac files and delete them. This corrupts the files on the AFP share. Pick the one type of share or service that makes the most sense for the types of clients accessing that volume, and use that single type of share or service. To support multiple types of shares, divide the volume into datasets and use one dataset per share.
This section demonstrates configuration and fine-tuning of AFP, NFS, SMB, WebDAV, and iSCSI shares. FTP and SSH configurations are described in Services.
9.5. Block (iSCSI)¶
iSCSI is a protocol standard for the consolidation of storage data. iSCSI allows TrueNAS® to act like a storage area network (SAN) over an existing Ethernet network. Specifically, it exports disk devices over an Ethernet network that iSCSI clients (called initiators) can attach to and mount. Traditional SANs operate over fibre channel networks which require a fibre channel infrastructure such as fibre channel HBAs, fibre channel switches, and discrete cabling. iSCSI can be used over an existing Ethernet network, although dedicated networks can be built for iSCSI traffic in an effort to boost performance. iSCSI also provides an advantage in an environment that uses Windows shell programs; these programs tend to filter “Network Location” but iSCSI mounts are not filtered.
Before configuring the iSCSI service, be familiar with this iSCSI terminology:
CHAP: an authentication method which uses a shared secret and three-way authentication to determine if a system is authorized to access the storage device and to periodically confirm that the session has not been hijacked by another system. In iSCSI, the initiator (client) performs the CHAP authentication.
Mutual CHAP: a superset of CHAP in that both ends of the communication authenticate to each other.
Initiator: a client which has authorized access to the storage data on the TrueNAS® system. The client requires initiator software to initiate the connection to the iSCSI share.
Target: a storage resource on the TrueNAS® system. Every target has a unique name known as an iSCSI Qualified Name (IQN).
Internet Storage Name Service (iSNS): protocol for the automated discovery of iSCSI devices on a TCP/IP network.
Extent: the storage unit to be shared. It can either be a file or a device.
Portal: indicates which IP addresses and ports to listen on for connection requests.
LUN: Logical Unit Number representing a logical SCSI device. An initiator negotiates with a target to establish connectivity to a LUN. The result is an iSCSI connection that emulates a connection to a SCSI hard disk. Initiators treat iSCSI LUNs as if they were a raw SCSI or SATA hard drive. Rather than mounting remote directories, initiators format and directly manage filesystems on iSCSI LUNs. When configuring multiple iSCSI LUNs, create a new target for each LUN. Since iSCSI multiplexes a target with multiple LUNs over the same TCP connection, there can be TCP contention when more than one target accesses the same LUN. TrueNAS® supports up to 1024 LUNs.
ALUA: Asymmetric Logical Unit Access allows a client computer to discover the best path to the storage on a TrueNAS® system. HA storage clusters can provide multiple paths to the same storage. For example, the disks are directly connected to the primary computer and provide high speed and bandwidth when accessed through that primary computer. The same disks are also available through the secondary computer, but because they are not directly connected to it, speed and bandwidth are restricted. With ALUA, clients automatically ask for and use the best path to the storage. If one of the TrueNAS® HA computers becomes inaccessible, the clients automatically switch to the next best alternate path to the storage. When a better path becomes available, as when the primary host becomes available again, the clients automatically switch back to that better path to the storage.
Note
Do not enable ALUA on TrueNAS® unless it is supported by and enabled on the client computers also. ALUA only works properly when enabled on both the client and server.
In TrueNAS®, iSCSI is built into the kernel. This version of iSCSI supports Microsoft Offloaded Data Transfer (ODX), meaning that file copies happen locally, rather than over the network. It also supports the VAAI (vStorage APIs for Array Integration) primitives for efficient operation of storage tasks directly on the NAS. To take advantage of the VAAI primitives, create a zvol using the instructions in Create zvol and use it to create a device extent, as described in Extents.
To configure iSCSI:
- Review the target global configuration parameters.
- Create at least one portal.
- Determine which hosts are allowed to connect using iSCSI and create an initiator.
- Decide if authentication will be used, and if so, whether it will be CHAP or mutual CHAP. If using authentication, create an authorized access.
- Create a target.
- Create either a device or a file extent to be used as storage.
- Associate a target with an extent.
- Start the iSCSI service in .
The rest of this section describes these steps in more detail.
Note
If the system has been licensed for Fibre Channel, the screens will vary slightly from those found in the rest of this section. Refer to the section on Fibre Channel Ports for details.
9.5.1. Target Global Configuration¶
, shown in Figure 9.5.1, contains settings that apply to all iSCSI shares. Table 9.5.1 summarizes the settings that are configured in the Target Global Configuration screen.
Some built-in values affect iSNS usage. Fetching of allowed initiators from iSNS is not implemented, so target ACLs must be configured manually. To make iSNS registration useful, iSCSI targets should have explicitly configured port IP addresses. This avoids initiators attempting to discover unconfigured target portal addresses like 0.0.0.0.
The iSNS registration period is 900 seconds. Registered Network Entities not updated during this period are unregistered. The timeout for iSNS requests is 5 seconds.
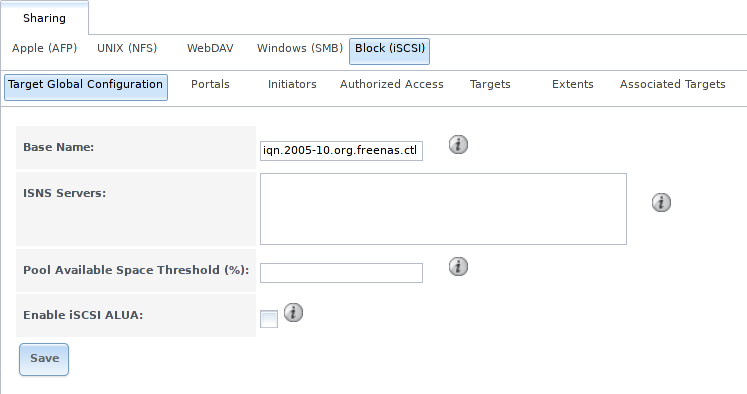
Fig. 9.5.1 iSCSI Target Global Configuration Variables
| Setting | Value | Description |
|---|---|---|
| Base Name | string | Lowercase alphanumeric characters plus dot (.), dash (-), and colon (:) are allowed. See the “Constructing iSCSI names using the iqn. format” section of RFC 3721. |
| ISNS Servers | string | Enter the hostnames or IP addresses of ISNS servers to be registered with iSCSI targets and portals of the system. Separate each entry with a space. |
| Pool Available Space Threshold | integer | Enter the percentage of free space to in the pool. When this percentage is reached, the system issues an alert, but only if zvols are used. See VAAI Threshold Warning for more information. |
| Enable iSCSI ALUA | checkbox | Enable ALUA for automatic best path discovery when supported by clients. This option is only available on HA systems. |
9.5.2. Portals¶
A portal specifies the IP address and port number to be used for iSCSI connections. brings up the screen shown in Figure 9.5.2.
Table 9.5.2 summarizes the settings that can be configured when adding a portal. To assign additional IP addresses to the portal, click the link Add extra Portal IP.
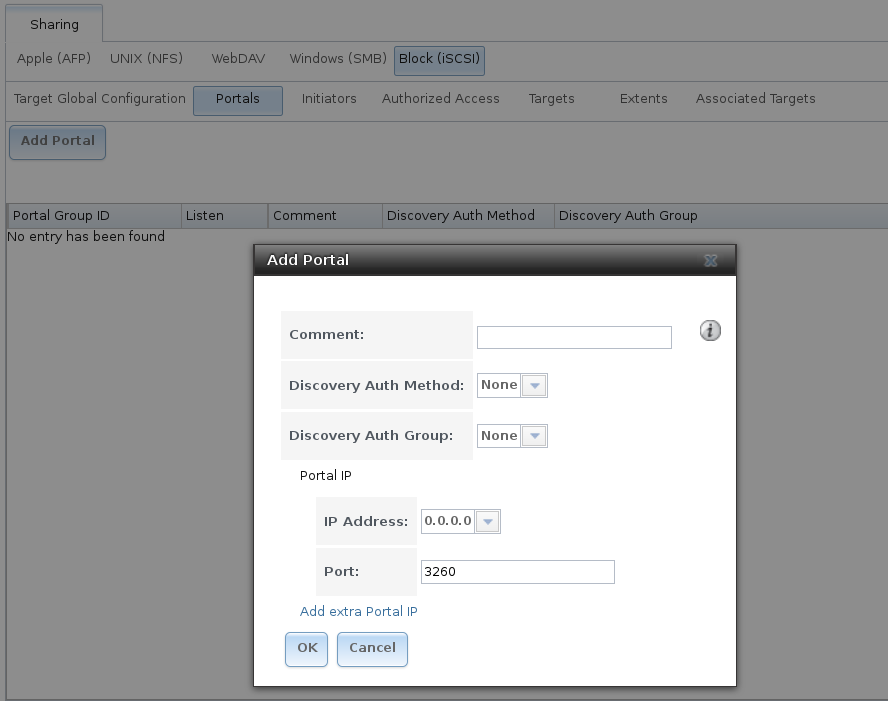
Fig. 9.5.2 Adding an iSCSI Portal
| Setting | Value | Description |
|---|---|---|
| Comment | string | Optional description. Portals are automatically assigned a numeric group ID. |
| Discovery Auth Method | drop-down menu | iSCSI supports multiple authentication methods that are used by the target to discover valid devices. None allows anonymous discovery while CHAP and Mutual CHAP both require authentication. |
| Discovery Auth Group | drop-down menu | Select a user created in Authorized Access if the Discovery Auth Method is set to CHAP or Mutual CHAP. |
| IP address | drop-down menu | Select the IPv4 or IPv6 address associated with an interface or the wildcard address of 0.0.0.0 (any interface). |
| Port | integer | TCP port used to access the iSCSI target. Default is 3260. |
TrueNAS® systems with multiple IP addresses or interfaces can use a portal to provide services on different interfaces or subnets. This can be used to configure multi-path I/O (MPIO). MPIO is more efficient than a link aggregation.
If the TrueNAS® system has multiple configured interfaces, portals can also be used to provide network access control. For example, consider a system with four interfaces configured with these addresses:
192.168.1.1/24
192.168.2.1/24
192.168.3.1/24
192.168.4.1/24
A portal containing the first two IP addresses (group ID 1) and a portal containing the remaining two IP addresses (group ID 2) could be created. Then, a target named A with a Portal Group ID of 1 and a second target named B with a Portal Group ID of 2 could be created. In this scenario, the iSCSI service would listen on all four interfaces, but connections to target A would be limited to the first two networks and connections to target B would be limited to the last two networks.
Another scenario would be to create a portal which includes every IP address except for the one used by a management interface. This would prevent iSCSI connections to the management interface.
9.5.3. Initiators¶
The next step is to configure authorized initiators, or the systems which are allowed to connect to the iSCSI targets on the TrueNAS® system. To configure which systems can connect, use , shown in Figure 9.5.3.
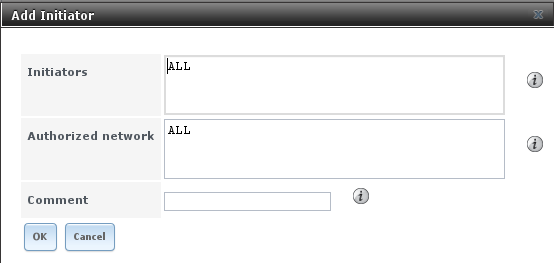
Fig. 9.5.3 Adding an iSCSI Initiator
Table 9.5.3 summarizes the settings that can be configured when adding an initiator.
| Setting | Value | Description |
|---|---|---|
| Initiators | string | Use ALL keyword or a list of initiator hostnames separated by spaces. |
| Authorized network | string | Network addresses that can use this initiator. Use ALL or
list network addresses with a CIDR mask.
Separate multiple addresses with a space:
192.168.2.0/24 192.168.2.1/12. |
| Comment | string | Notes or a description of the initiator. |
In the example shown in Figure 9.5.4, two groups are created. Group 1 allows connections from any initiator on any network. Group 2 allows connections from any initiator on the 10.10.1.0/24 network. Click an initiator’s entry to display its Edit and Delete buttons.
Note
Attempting to delete an initiator causes a warning that indicates if any targets or target/extent mappings depend upon the initiator. Confirming the delete causes these to be deleted also.
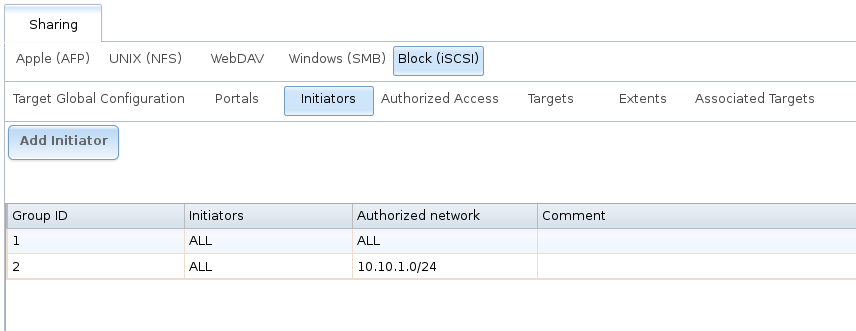
Fig. 9.5.4 Sample iSCSI Initiator Configuration
9.5.4. Authorized Accesses¶
When using CHAP or mutual CHAP to provide authentication, creating an authorized access in is recommended. This screen is shown in Figure 9.5.5.
Note
This screen sets login authentication. This is different from discovery authentication which is set in Target Global Configuration.
Fig. 9.5.5 Adding an iSCSI Authorized Access
Table 9.5.4 summarizes the settings that can be configured when adding an authorized access:
| Setting | Value | Description |
|---|---|---|
| Group ID | integer | Allows different groups to be configured with different authentication profiles. Example: all users with a Group ID of 1 will inherit the authentication profile associated with Group 1. |
| User | string | Enter name of user account to create for CHAP authentication with the user on the remote system. Many initiators default to using the initiator name as the user. |
| Secret | string | Enter a password for User. The iSCSI standard requires that this be between 12 and 16 characters. |
| Peer User | string | Only input when configuring mutual CHAP. In most cases it will need to be the same value as User. |
| Peer Secret | string | Enter the mutual secret password which must be different than the Secret. Required if Peer User is set. |
Note
CHAP does not work with GlobalSAN initiators on macOS.
As authorized accesses are added, they will be listed under View Authorized Accesses. In the example shown in Figure 9.5.6, three users (test1, test2, and test3) and two groups (1 and 2) are created, with group 1 consisting of one CHAP user and group 2 consisting of one mutual CHAP user and one CHAP user. Click an authorized access entry to display its Edit and Delete buttons.
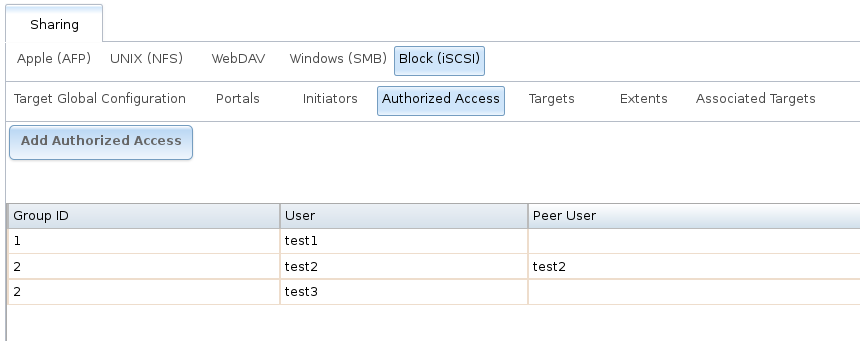
Fig. 9.5.6 Viewing Authorized Accesses
9.5.5. Targets¶
Next, create a Target using , as shown in Figure 9.5.7. A target combines a portal ID, allowed initiator ID, and an authentication method. Table 9.5.5 summarizes the settings that can be configured when creating a Target.
Note
An iSCSI target creates a block device that may be accessible to multiple initiators. A clustered filesystem is required on the block device, such as VMFS used by VMware ESX/ESXi, in order for multiple initiators to mount the block device read/write. If a traditional filesystem such as EXT, XFS, FAT, NTFS, UFS, or ZFS is placed on the block device, care must be taken that only one initiator at a time has read/write access or the result will be filesystem corruption. If multiple clients need access to the same data on a non-clustered filesystem, use SMB or NFS instead of iSCSI, or create multiple iSCSI targets (one per client).
Fig. 9.5.7 Adding an iSCSI Target
| Setting | Value | Description |
|---|---|---|
| Target Name | string | Required. The base name is automatically prepended if the target name does not start with iqn. Lowercase alphanumeric characters plus dot (.), dash (-), and colon (:) are allowed. See the “Constructing iSCSI names using the iqn. format” section of RFC 3721. |
| Target Alias | string | Enter an optional user-friendly name. |
| Portal Group ID | drop-down menu | Leave empty or select number of existing portal to use. |
| Initiator Group ID | drop-down menu | Select which existing initiator group has access to the target. |
| Auth Method | drop-down menu | Choices are: None, Auto, CHAP, or Mutual CHAP. |
| Authentication Group number | drop-down menu | Select None or an integer. This number represents the number of existing authorized accesses. |
9.5.6. Extents¶
iSCSI targets provide virtual access to resources on the TrueNAS® system. Extents are used to define resources to share with clients. There are two types of extents: device and file.
Device extents provide virtual storage access to zvols, zvol snapshots, or physical devices like a disk, an SSD, a hardware RAID volume, or a HAST device.
File extents provide virtual storage access to an individual file.
Tip
For typical use as storage for virtual machines where the virtualization software is the iSCSI initiator, device extents with zvols provide the best performance and most features. For other applications, device extents sharing a raw device can be appropriate. File extents do not have the performance or features of device extents, but do allow creating multiple extents on a single filesystem.
Virtualized zvols support all the TrueNAS® VAAI primitives and are recommended for use with virtualization software as the iSCSI initiator.
The ATS, WRITE SAME, XCOPY and STUN, primitives are supported by both file and device extents. The UNMAP primitive is supported by zvols and raw SSDs. The threshold warnings primitive is fully supported by zvols and partially supported by file extents.
Virtualizing a raw device like a single disk or hardware RAID volume limits performance to the abilities of the device. Because this bypasses ZFS, such devices do not benefit from ZFS caching or provide features like block checksums or snapshots.
Virtualizing a zvol adds the benefits of ZFS, such as read and write cache. Even if the client formats a device extent with a different filesystem, the data still resides on a ZFS volume and benefits from ZFS features like block checksums and snapshots.
Warning
For performance reasons and to avoid excessive fragmentation, keep the used space of the pool below 80% when using iSCSI. The capacity of an existing extent can be increased as shown in Growing LUNs.
To add an extent, go to
.
In the example shown in
Figure 9.5.8,
the device extent is using the export zvol that was previously
created from the /mnt/volume1 volume.
Table 9.5.6 summarizes the settings that can be configured when creating an extent. Note that file extent creation fails when the name of the file to be created to the volume/dataset name. is not appended.
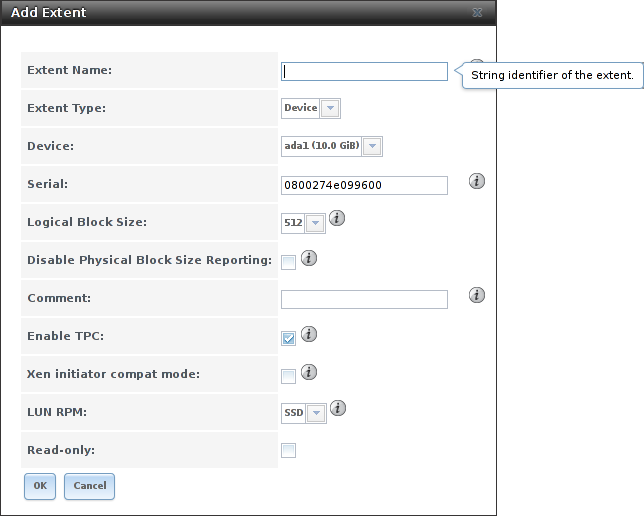
Fig. 9.5.8 Adding an iSCSI Extent
| Setting | Value | Description |
|---|---|---|
| Extent Name | string | Enter the extent name. If the Extent size is not 0, it cannot be an existing file within the volume/dataset. |
| Extent Type | drop-down menu | Select from File or Device. |
| Device | drop-down menu | Only appears if Device is selected. Select the unformatted disk, controller, zvol, zvol snapshot, or HAST device. |
| Serial | string | Unique LUN ID. The default is generated from the system MAC address. |
| Path to the extent | browse button | Only appears if File is selected. Browse to an existing file and use 0 as the Extent size, or browse to the volume or dataset, click Close, append the Extent Name to the path, and specify a value in Extent size. Extents cannot be created inside the jail root directory. |
| Extent size | integer | Only appears if File is selected. If the size is specified as 0, the file must already exist and the actual file size will be used. Otherwise, specify the size of the file to create. |
| Logical Block Size | drop-down menu | Only override the default if the initiator requires a different block size. |
| Disable Physical Block Size Reporting | checkbox | Set if the initiator does not support physical block size values over 4K (MS SQL). Setting can also prevent constant block size warnings when using this share with ESXi. |
| Available Space Threshold | string | Only appears if File or a zvol is selected. When the specified percentage of free space is reached, the system issues an alert. See VAAI Threshold Warning for more information. |
| Comment | string | Enter an optional comment. |
| Enable TPC | checkbox | If enabled, an initiator can bypass normal access control and access any scannable target. This allows xcopy operations otherwise blocked by access control. |
| Xen initiator compat mode | checkbox | Set this option when using Xen as the iSCSI initiator. |
| LUN RPM | drop-down menu | Do NOT change this setting when using Windows as the initiator. Only needs to be changed in large environments where the number of systems using a specific RPM is needed for accurate reporting statistics. |
| Read-only | checkbox | Set to prevent the initiator from initializing this LUN . |
9.5.7. Target/Extents¶
The last step is associating an extent to a target within . This screen is shown in Figure 9.5.9. Use the drop-down menus to select the existing target and extent. Click OK to add an entry for the LUN.
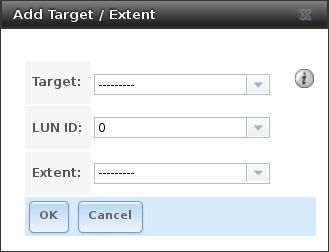
Fig. 9.5.9 Associating a Target With an Extent
Table 9.5.7 summarizes the settings that can be configured when associating targets and extents.
| Setting | Value | Description |
|---|---|---|
| Target | drop-down menu | Select an existing target. |
| LUN ID | integer | Type a value between 0 and 1023. Note that some initiators expect a value below 256. Enter 0 to statically assign the next available ID. |
| Extent | drop-down menu | Select an existing extent. |
Always associating extents to targets in a one-to-one manner is recommended, even though the GUI will allow multiple extents to be associated with the same target.
Note
Each LUN entry has Edit and Delete buttons for modifying the settings or deleting the LUN entirely. A verification popup appears when the Delete button is clicked. If an initiator has an active connection to the LUN, it is indicated in red text. Clearing initiator connections to a LUN before deleting it is recommended.
After iSCSI has been configured, remember to start it in . Click the red OFF button next to iSCSI. After a second or so, it will change to a blue ON, indicating that the service has started.
9.5.8. Fibre Channel Ports¶
If the TrueNAS® system has Fibre Channel ports, will appear as and an extra Fibre Channel Ports tab is added. An example is shown in Figure 9.5.10.
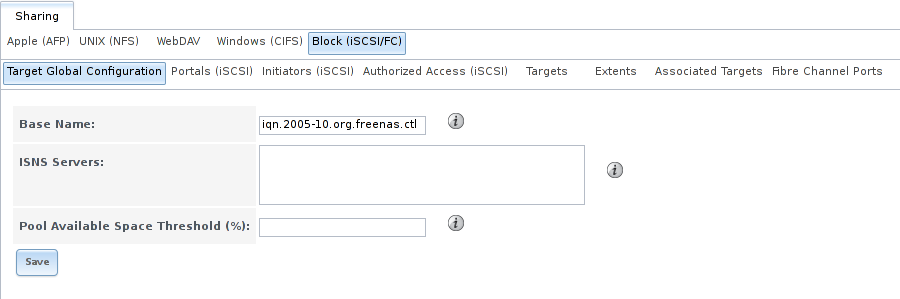
Fig. 9.5.10 Block (iSCSI) Screen
Otherwise, the Target Global Configuration screen is the same as described in Target Global Configuration.
Since the Portals, Initiators, and Authorized Access screens only apply to iSCSI, they are marked as such and can be ignored when configuring Fibre Channel.
As seen in Figure 9.5.11, the screen has an extra Target Mode option for indicating whether the target to create is iSCSI, Fibre Channel, or both.
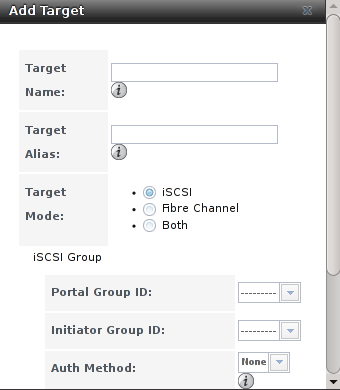
Fig. 9.5.11 Add Target Screen
After selecting Fibre Channel, this screen changes so only the Target Name and Target Alias fields remain, as those are the only applicable fields for a Fibre Channel connection. An example is shown in Figure 9.5.12.
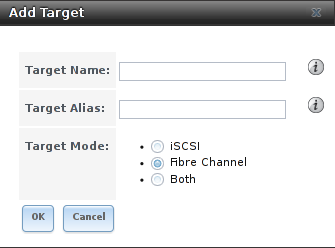
Fig. 9.5.12 Configuring a Fibre Channel Target
The screens for adding an extent and associating a target are the same as described in Extents and Target/Extents.
An example of the Fibre Channel Ports screen is shown in Figure 9.5.13.
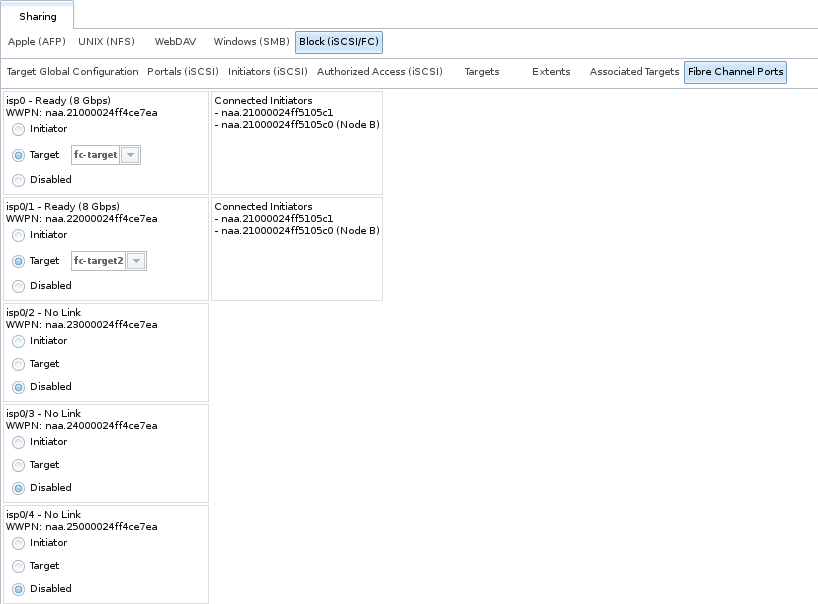
Fig. 9.5.13 Configuring a Fibre Channel Port
This screen shows the status of each attached fibre channel port, where:
- Initiator: indicates that the port is acting as a client and has access to any physically attached storage.
- Target: indicates that clients are connecting to the specified target through this port.
- Disabled: indicates that this fibre channel port is not in use.
Note
The Target tab of Reporting provides Fibre Channel port bandwidth graphs.
This example has also been configured for NPIV (N_Port ID Virtualization). Note that the physical interface isp0 has two virtual ports (isp0/1 and isp0/2) displayed in Figure 9.5.13:. NPIV allows the administrator to use switch zoning to configure each virtual port as if it was a physical port in order to provide access control. This is important in an environment with a mix of Windows systems and virtual machines in order to prevent automatic or accidental reformatting of targets containing unrecognized filesystems. It can also be used to segregate data; for example, to prevent the engineering department from accessing data from the human resources department. Refer to the switch documentation for details on how to configure zoning of virtual ports.
To create the virtual ports on the TrueNAS® system, go to and enter the following:
- Variable: input hint.isp.X.vports, replacing X with the number of the physical interface.
- Value: input the number of virtual ports to create. Note that there cannot be more then 125 SCSI target ports and that number includes all physical Fibre Channel ports, all virtual ports, and all configured combinations of iSCSI portals and targets.
- Type: make sure loader is selected.
In the example shown in Figure 9.5.14, two physical interfaces were each assigned 4 virtual ports. Note that two tunables were required, one for each physical interface. After the tunables are created, the configured number of virtual ports appears in the Fibre Channel Ports screen so they can be associated with targets. They will also be advertised to the switch so zoning can be configured on the switch. After a virtual port has been associated with a target, it is added to the Target tab of Reporting where its bandwidth usage can be viewed.
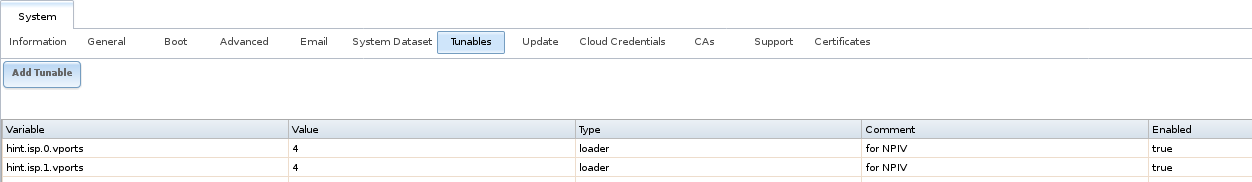
Fig. 9.5.14 Adding Virtual Ports
9.5.9. Connecting to iSCSI¶
To access the iSCSI target, clients must use iSCSI initiator software.
An iSCSI Initiator client is pre-installed with Windows 7. A detailed how-to for this client can be found here. A client for Windows 2000, XP, and 2003 can be found here. This how-to shows how to create an iSCSI target for a Windows 7 system.
macOS does not include an initiator. globalSAN is a commercial, easy-to-use Mac initiator.
BSD systems provide command line initiators: iscontrol(8) comes with FreeBSD versions 9.x and lower, iscsictl(8) comes with FreeBSD versions 10.0 and higher, iscsi-initiator(8) comes with NetBSD, and iscsid(8) comes with OpenBSD.
Some Linux distros provide the command line utility iscsiadm from Open-iSCSI. Use a web search to see if a package exists for the distribution should the command not exist on the Linux system.
If a LUN is added while iscsiadm is already connected, it will not see the new LUN until rescanned with iscsiadm -m node -R. Alternately, use iscsiadm -m discovery -t st -p portal_IP to find the new LUN and iscsiadm -m node -T LUN_Name -l to log into the LUN.
Instructions for connecting from a VMware ESXi Server can be found at How to configure FreeNAS 8 for iSCSI and connect to ESX(i). Note that the requirements for booting vSphere 4.x off iSCSI differ between ESX and ESXi. ESX requires a hardware iSCSI adapter while ESXi requires specific iSCSI boot firmware support. The magic is on the booting host side, meaning that there is no difference to the TrueNAS® configuration. See the iSCSI SAN Configuration Guide for details.
The VMware firewall only allows iSCSI connections on port 3260 by default. If a different port has been selected, outgoing connections to that port must be manually added to the firewall before those connections will work.
If the target can be seen but does not connect, check the Discovery Auth settings in Target Global Configuration.
If the LUN is not discovered by ESXi, make sure that promiscuous mode is set to Accept in the vSwitch.
9.5.10. Growing LUNs¶
The method used to grow the size of an existing iSCSI LUN depends on whether the LUN is backed by a file extent or a zvol. Both methods are described in this section.
Enlarging a LUN with one of the methods below gives it more unallocated space, but does not automatically resize filesystems or other data on the LUN. This is the same as binary-copying a smaller disk onto a larger one. More space is available on the new disk, but the partitions and filesystems on it must be expanded to use this new space. Resizing virtual disk images is usually done from virtual machine management software. Application software to resize filesystems is dependent on the type of filesystem and client, but is often run from within the virtual machine. For instance, consider a Windows VM with the last partition on the disk holding an NTFS filesystem. The LUN is expanded and the partition table edited to add the new space to the last partition. The Windows disk manager must still be used to resize the NTFS filesystem on that last partition to use the new space.
9.5.10.1. Zvol Based LUN¶
To grow a zvol based LUN, go to , highlight the zvol to be grown, and click Edit zvol. In the example shown in Figure 9.5.15, the current size of the zvol named zvol1 is 4 GiB.
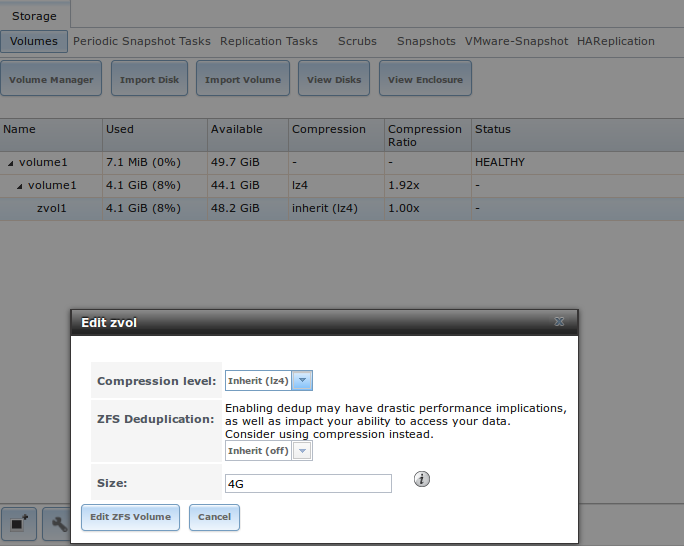
Fig. 9.5.15 Editing an Existing Zvol
Enter the new size for the zvol in the Size field and click Edit ZFS Volume. This menu closes and the new size for the zvol is immediately shown in the Used column of the View Volumes screen.
Note
The GUI does not allow reducing (shrinking) the size of the zvol, as doing so could result in loss of data. It also does not allow increasing the size of the zvol past 80% of the volume size.
9.5.10.2. File Extent Based LUN¶
To grow a file extent based LUN, go to
to determine the path of the file extent to
grow. Open Shell to grow the extent. This example
grows /mnt/volume1/data by 2 G:
truncate -s +2g /mnt/volume1/data
Go back to and click the Edit button for the file extent. Set the size to 0 as this causes the iSCSI target to use the new size of the file.