tnuser9999
Dabbler
- Joined
- Jun 29, 2023
- Messages
- 40
I'm currently testing Truenas ZFS replication as a backup solution. My aim is to ensure that ZFS snapshots are not deleted on the destination server when they are removed from the source. This is crucial to prevent potential data loss if unauthorized access occurs.
In my replication configuration, I selected a custom snapshot retention policy to prevent source snapshot actions from affecting the snapshots on the destination server. However, during a test where I rolled back the source to a previous snapshot, I noticed that the corresponding snapshots on the destination were also removed. This unexpected behavior occurred consistently in multiple tests.
Could someone please advise me on the correct configuration to ensure that changes on the source do not lead to snapshot removals on the destination? Your insights would be greatly appreciated.
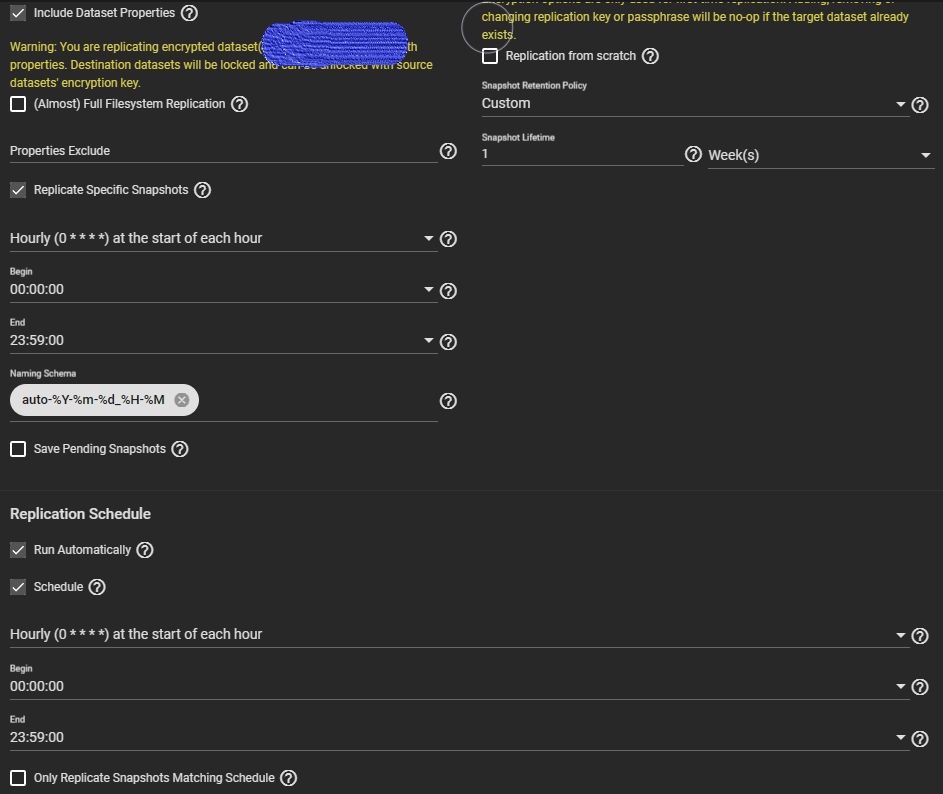
In my replication configuration, I selected a custom snapshot retention policy to prevent source snapshot actions from affecting the snapshots on the destination server. However, during a test where I rolled back the source to a previous snapshot, I noticed that the corresponding snapshots on the destination were also removed. This unexpected behavior occurred consistently in multiple tests.
Could someone please advise me on the correct configuration to ensure that changes on the source do not lead to snapshot removals on the destination? Your insights would be greatly appreciated.
