asw2012
Contributor
- Joined
- Dec 17, 2012
- Messages
- 182
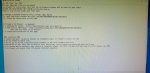
2 days ago my 9 yr. old son unknowingly clicked on a popup from either one of those .io games or through Roblox somehow. I don't know exactly where it came from, but he clicked it and WHAM... all files on my computer, networked computers and my shared FreeNAS folders got locked/encrypted (*.locked extension) with the txt file that I took a snapshot of (attached). Luckily I almost immediately noticed because the movie I was watching on EMBY stopped playing - because those files got nailed too! Did some digging, found the files (*.locked) and that txt file at that time.
Immideately unplugged my cable modem and router so that virus / trojan can't spread any further, then unplugged all RJ45 router connections - but damage was already done. Well also, unfortunately, part of the shared folders on my FreeNAS box were the Acronis backups that I do 1x a week on all of my computers. Those were all inaccessible, (*.locked).
So, turned my router on, used an old laptop that was not plugged in at the time, got access to my FreeNAS GUI, reverted to the snapshots I took 3 days earlier. I take 2x snapshots per week on everything :) - all files on my FreeNAS box are OK now - including the important Acronis backups :)
Transferred my Acronis backups to my 2TB portable. Booted up each computer with the Acronis, restored all hard drives and about 6 hours later, up and running like nothing ever happened, with the exception of the 3 days of lost info (not a big deal).
Even if those steps did not work, I use Backblaze for offsite backups. It would have taken much more time, but I still would have saved all of my computers and FreeNAS storage.
All the while I was doing this, I showed my 9yr old son all of the steps I took above and made sure he understood (for the most part). He now knows not to click on funny stuff anymore - AND he knows the consequences!
Immideately unplugged my cable modem and router so that virus / trojan can't spread any further, then unplugged all RJ45 router connections - but damage was already done. Well also, unfortunately, part of the shared folders on my FreeNAS box were the Acronis backups that I do 1x a week on all of my computers. Those were all inaccessible, (*.locked).
So, turned my router on, used an old laptop that was not plugged in at the time, got access to my FreeNAS GUI, reverted to the snapshots I took 3 days earlier. I take 2x snapshots per week on everything :) - all files on my FreeNAS box are OK now - including the important Acronis backups :)
Transferred my Acronis backups to my 2TB portable. Booted up each computer with the Acronis, restored all hard drives and about 6 hours later, up and running like nothing ever happened, with the exception of the 3 days of lost info (not a big deal).
Even if those steps did not work, I use Backblaze for offsite backups. It would have taken much more time, but I still would have saved all of my computers and FreeNAS storage.
All the while I was doing this, I showed my 9yr old son all of the steps I took above and made sure he understood (for the most part). He now knows not to click on funny stuff anymore - AND he knows the consequences!