GIZMO_the_Great
Cadet
- Joined
- Mar 20, 2015
- Messages
- 6
Hi
Further to this thread , I have decided to buy a second router for my home network.
Currently, I have one commercial grade router provided by my broadband supplier. It's quite good and has an OK firewall, but it lacks some of the features I need - most notably, concise IP address filtering\blocking\banning. Internally, it is the default gateway and all internal traffic routes through it. I need to SSH to my FreeNAS from outside my internal network occasionally, as well as from inside it.
I will soon have a D-Link router (again, fairly consumer level) that I intend to install DD-WRT on (having used that before some years ago) which will give me these more advanced filtering and blocking features.
However, I have a question based on my options.
I could but the current router into "modem mode" and connect the D-Link to it as the routing device meaning I discard the capabilities of the first router in favour of the second (the first therefore just provides the high speed connection). All my internal devices would then connect to the D-Link router instead (inc my FreeNAS server) and go Internet bound over the modem mode of the original. So my network topology would remain the same but I get some additional features for the safety of the FreeNAS.
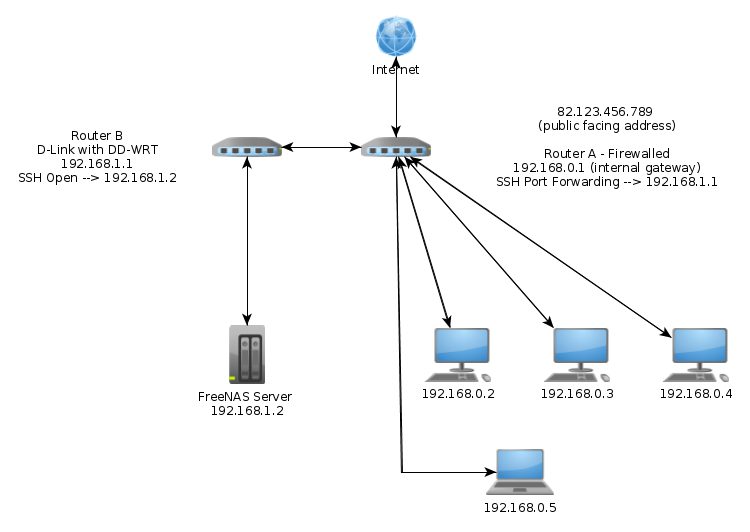
Or, I could leave the first router in place for all my other devices EXCEPT the FreeNAS and configure the D-Link specifically for my FreeNAS system. In other words, traffic arrives at my first router and anything for FreeNas gets routed to the D-Link router, where any IP address filtering\blocking\banning etc can take place before any legitimate traffic is sent onward to FreeNAS. This has the effect of isolating the rest of my network meaning they are all protected as they are now (with no public facing open ports) but I can still communicate with the FreeNAS from my internal machines via the two routers.
To me, the second option seems the most preferable, but it is also more complicated and I have little experience of such configurations.
So my question is which option would you go with and are there any fairly simple HOW TO guides for this configuration? To simplify this rather long winded explanation I have created two diagrams :
Diagram A shows my current setup and Diagram B shows my proposed second option. From the diagram, does it look like I am on the right lines or is it all a bad idea? I want to keep things simple but equally I want to ensure that my FreeNAS and network system is protected once I allow SSH connections to the FreeNAS from the outside world.
Diagram A
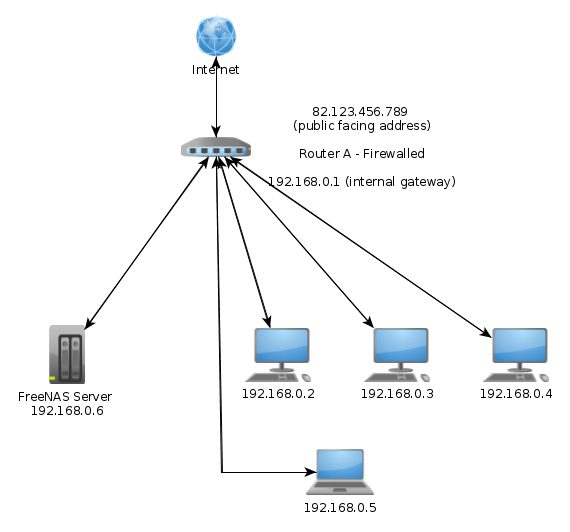
Diagram B
Further to this thread , I have decided to buy a second router for my home network.
Currently, I have one commercial grade router provided by my broadband supplier. It's quite good and has an OK firewall, but it lacks some of the features I need - most notably, concise IP address filtering\blocking\banning. Internally, it is the default gateway and all internal traffic routes through it. I need to SSH to my FreeNAS from outside my internal network occasionally, as well as from inside it.
I will soon have a D-Link router (again, fairly consumer level) that I intend to install DD-WRT on (having used that before some years ago) which will give me these more advanced filtering and blocking features.
However, I have a question based on my options.
I could but the current router into "modem mode" and connect the D-Link to it as the routing device meaning I discard the capabilities of the first router in favour of the second (the first therefore just provides the high speed connection). All my internal devices would then connect to the D-Link router instead (inc my FreeNAS server) and go Internet bound over the modem mode of the original. So my network topology would remain the same but I get some additional features for the safety of the FreeNAS.
Or, I could leave the first router in place for all my other devices EXCEPT the FreeNAS and configure the D-Link specifically for my FreeNAS system. In other words, traffic arrives at my first router and anything for FreeNas gets routed to the D-Link router, where any IP address filtering\blocking\banning etc can take place before any legitimate traffic is sent onward to FreeNAS. This has the effect of isolating the rest of my network meaning they are all protected as they are now (with no public facing open ports) but I can still communicate with the FreeNAS from my internal machines via the two routers.
To me, the second option seems the most preferable, but it is also more complicated and I have little experience of such configurations.
So my question is which option would you go with and are there any fairly simple HOW TO guides for this configuration? To simplify this rather long winded explanation I have created two diagrams :
Diagram A shows my current setup and Diagram B shows my proposed second option. From the diagram, does it look like I am on the right lines or is it all a bad idea? I want to keep things simple but equally I want to ensure that my FreeNAS and network system is protected once I allow SSH connections to the FreeNAS from the outside world.
Diagram A
Diagram B
