short-stack
Explorer
- Joined
- Feb 28, 2017
- Messages
- 80
I recently switched out my firewall and started putting more restrictive rules outbound in place and I noticed that some of my Jail traffic was coming in to my firewall on the wrong interface. I have several VLANs that connect from firewall to switch and from switch to NAS over carrying several VLANs.
After some troubleshooting to identify where problem was being initiated, it's only on Jails that don't utilize VNET. All of my virtual machines, and any jail that has VNET are tagged appropriately, but a standard jail that is configured on a specific VLAN is sending traffic out tagged with VLAN 1,
It worked for years, but I wasn't running anti-spoofing or restrictive outbound rules on the firewall so it seemingly worked itself out coming in to the firewall on the native VLAN and going back out on the VLAN interface.
I monitored a SPAN port on the switch where my NAS is connected and took a packet capture to look at how the VLAN tagging was being applied.
The screenshots below show a TCP connection where I did a simple curl of google.com on a standard jail, a jail with VNET, and a VM.
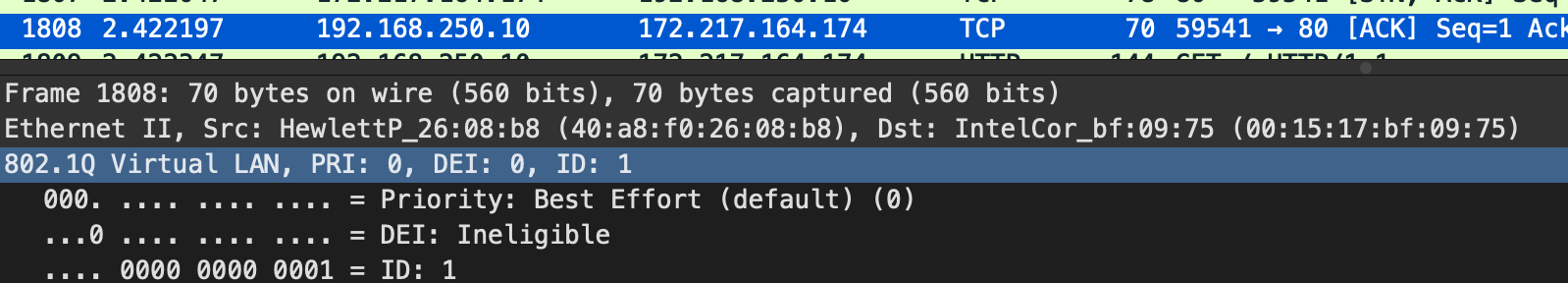
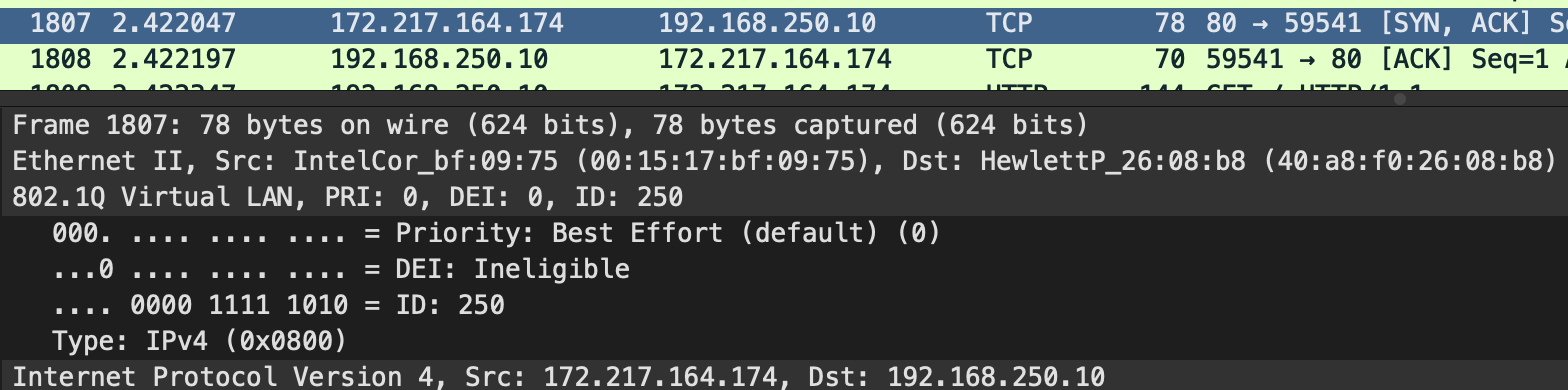
On the standard jail, the packets are tagged VLAN1 on the way out, but you can see VLAN 250 on the way back in.
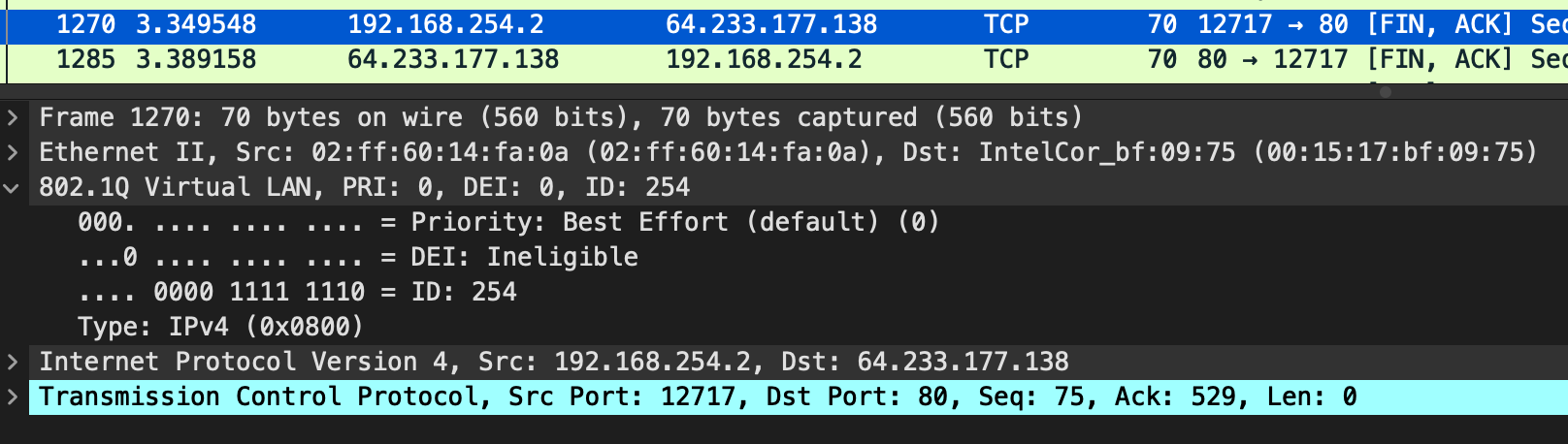
This is a jail on VLAN 254 that uses VNET that is being tagged appropriately.
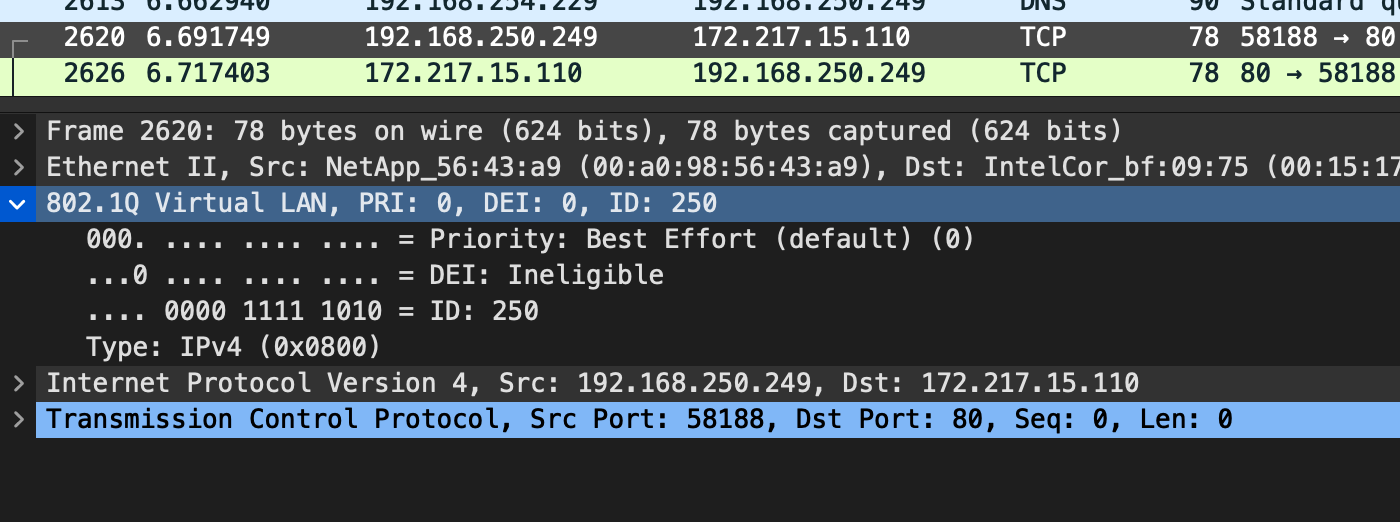
This is a VM on VLAN 250 that is being tagged appropriately.
If anyone has any ideas, or if I missed a configuration item I'd being interested to hear them.
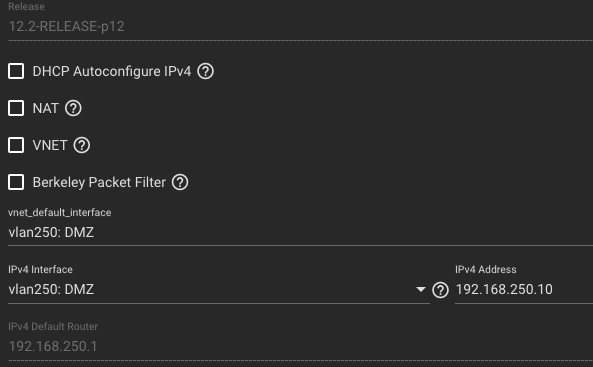
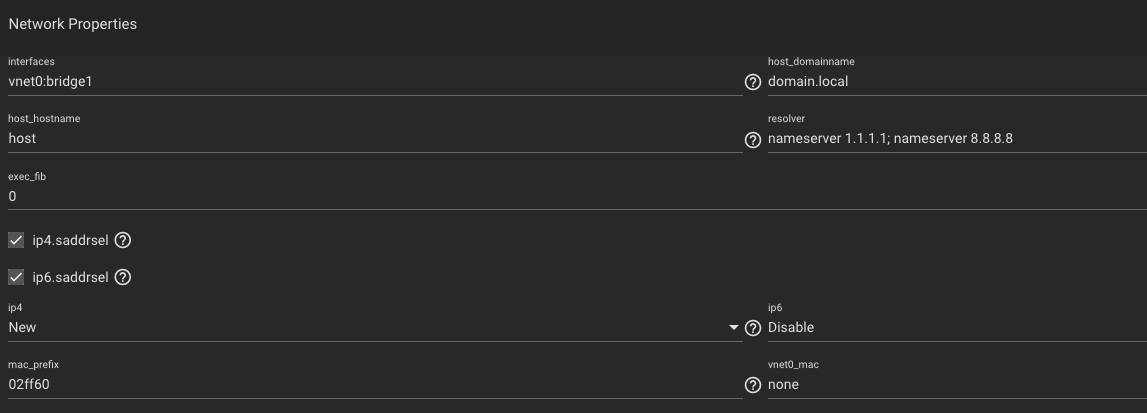
Here are the basic and network settings for the jail in question:
After some troubleshooting to identify where problem was being initiated, it's only on Jails that don't utilize VNET. All of my virtual machines, and any jail that has VNET are tagged appropriately, but a standard jail that is configured on a specific VLAN is sending traffic out tagged with VLAN 1,
It worked for years, but I wasn't running anti-spoofing or restrictive outbound rules on the firewall so it seemingly worked itself out coming in to the firewall on the native VLAN and going back out on the VLAN interface.
I monitored a SPAN port on the switch where my NAS is connected and took a packet capture to look at how the VLAN tagging was being applied.
The screenshots below show a TCP connection where I did a simple curl of google.com on a standard jail, a jail with VNET, and a VM.
On the standard jail, the packets are tagged VLAN1 on the way out, but you can see VLAN 250 on the way back in.
This is a jail on VLAN 254 that uses VNET that is being tagged appropriately.
This is a VM on VLAN 250 that is being tagged appropriately.
If anyone has any ideas, or if I missed a configuration item I'd being interested to hear them.
Here are the basic and network settings for the jail in question:


