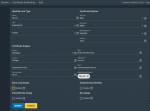
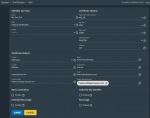
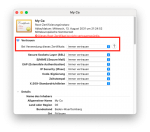
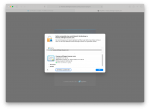
Okay the Certificate part of Truenas is broken.
And it's broken since several releases. At first I thought it was a problem with navigators not accepting private CA anymore but it's not.
I used several certificates from the same Truenas internal CA and it used to work until some months agos. That CA was created in the Freenas times and is valid until 2026 or like.
At least the default setup is broken and maybe it is now needed to specify some options that are not defaults.
I tried hard today issuing a certificate for an internal lab server but no way to get it working. Certificate is allways stated as invalid for browsers (firefox and chrome on linux, windows and android).
So I gave a try on pfsense certificate authority and it worked like a charm. Same server, same CN, same SAN, same ... Of course I had to set lifetime of 398 days since Apple forced the rest of the world to use that limit but I had it set on both pfsense and Truenas so that's not the point.
Very easy to reproduce : create a CA, create certificate, export CA, certificate and key. Import CA on browser/OS. Configure server with issued certificate and try to access it. Truenas certificate : invalid, Pfsense : ok.
So the Truenas certificates are somehow broken. Maybe it's only a matter of options that have now to be set and are not set or something else.
So now I have a Pfsense server certificate the Truenas server. What else ?
And it's broken since several releases. At first I thought it was a problem with navigators not accepting private CA anymore but it's not.
I used several certificates from the same Truenas internal CA and it used to work until some months agos. That CA was created in the Freenas times and is valid until 2026 or like.
At least the default setup is broken and maybe it is now needed to specify some options that are not defaults.
I tried hard today issuing a certificate for an internal lab server but no way to get it working. Certificate is allways stated as invalid for browsers (firefox and chrome on linux, windows and android).
So I gave a try on pfsense certificate authority and it worked like a charm. Same server, same CN, same SAN, same ... Of course I had to set lifetime of 398 days since Apple forced the rest of the world to use that limit but I had it set on both pfsense and Truenas so that's not the point.
Very easy to reproduce : create a CA, create certificate, export CA, certificate and key. Import CA on browser/OS. Configure server with issued certificate and try to access it. Truenas certificate : invalid, Pfsense : ok.
So the Truenas certificates are somehow broken. Maybe it's only a matter of options that have now to be set and are not set or something else.
So now I have a Pfsense server certificate the Truenas server. What else ?