strawdog74
Dabbler
- Joined
- May 23, 2012
- Messages
- 42
After previously having my tv-daemon & mysql installed on the main FreeNAS partition (which worked great), I have finally decided to bite the bullet and use a JAIL as its the recommended method.
The thing is, I've followed all the steps here but I can't connect via SSH to the JAIL using the IP address I set it to. THe IP address is definitely on the same SUBNET as the router & laptop I am using, but it doesn't seem to be working.
FREENAS = 192.168.1.50
JAIL = 192.168.1.55
GATEWAY = 192.168.1.254
The JAIL is responding to PING commands, and I am assuming the JAIL supports SSH & SFTP from the off, as there doesn't appear to be PBI files for these.
Anyone any ideas how I can connect to my JAIL via SSH or SFTP?
PING RESULTS are as follows :-
MESSAGES LOG is as follows :-
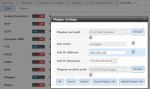
Jail configuration details are as follows :-
The thing is, I've followed all the steps here but I can't connect via SSH to the JAIL using the IP address I set it to. THe IP address is definitely on the same SUBNET as the router & laptop I am using, but it doesn't seem to be working.
FREENAS = 192.168.1.50
JAIL = 192.168.1.55
GATEWAY = 192.168.1.254
The JAIL is responding to PING commands, and I am assuming the JAIL supports SSH & SFTP from the off, as there doesn't appear to be PBI files for these.
Anyone any ideas how I can connect to my JAIL via SSH or SFTP?
PING RESULTS are as follows :-
Code:
Pinging 192.168.1.55 with 32 bytes of data:
Reply from 192.168.1.55: bytes=32 time=5ms TTL=64
Reply from 192.168.1.55: bytes=32 time=2ms TTL=64
Reply from 192.168.1.55: bytes=32 time=2ms TTL=64
Reply from 192.168.1.55: bytes=32 time=2ms TTL=64
Ping statistics for 192.168.1.55:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 2ms, Maximum = 5ms, Average = 2ms
MESSAGES LOG is as follows :-
Code:
Feb 18 17:47:54 freenas notifier: security.jail.allow_raw_sockets: 0 -> 1 Feb 18 17:47:54 freenas notifier: Configuring jails: sysvipc_allow=YES. Feb 18 17:47:54 freenas notifier: Starting jails: packages. Feb 18 17:47:54 freenas kernel: bridge0: Ethernet address: 02:d8:6a:44:4b:00 Feb 18 17:47:54 freenas kernel: epair0a: Ethernet address: 02:e8:fc:00:0a:0a Feb 18 17:47:54 freenas kernel: epair0b: Ethernet address: 02:e8:fc:00:0b:0b Feb 18 17:47:54 freenas kernel: epair0a: link state changed to UP Feb 18 17:47:54 freenas kernel: epair0b: link state changed to UP Feb 18 17:47:54 freenas kernel: epair0a: promiscuous mode enabled Feb 18 17:47:54 freenas notifier: add net default: gateway 192.168.1.254 Feb 18 17:47:54 freenas notifier: stty: stdin isn't a terminal Feb 18 17:47:54 freenas kernel: bge0: promiscuous mode enabled Feb 18 17:47:54 freenas notifier: /etc/rc: WARNING: $hostname is not set -- see rc.conf(5). Feb 18 17:47:54 freenas notifier: Generating host.conf. Feb 18 17:47:54 freenas notifier: ELF ldconfig path: /lib /usr/lib /usr/local/lib Feb 18 17:47:54 freenas notifier: 32-bit compatibility ldconfig path: /usr/lib32 Feb 18 17:47:54 freenas notifier: Creating and/or trimming log files. Feb 18 17:47:54 freenas notifier: Starting syslogd. Feb 18 17:47:54 freenas notifier: Clearing /tmp (X related). Feb 18 17:47:54 freenas notifier: Updating motd:. Feb 18 17:47:55 freenas notifier: Starting cron. Feb 18 17:47:55 freenas notifier: Feb 18 17:47:55 freenas notifier: Mon Feb 18 17:47:55 GMT 2013
Jail configuration details are as follows :-

