Looking for guidance. I upgraded from 11.2-U7 to 11.3 RELEASE and found I could not un-encrypt my pool (named "Pool") with the passphrase or the key, geli.key. Immediately I reverted back to 11.2-U7, but still could not un-encrypt the pool. Next I exported the pool thinking that if I re-import it I might be able to un-encrypt it (perhaps unwisely). When attempting to import the pool, the pool would not show up in the import dialog.
I next moved to another prior release (don't remember which one) where the encrypted pool was already showing in the dashboard (didn't need to be imported). Upon attempting to unlock it I got this error message:
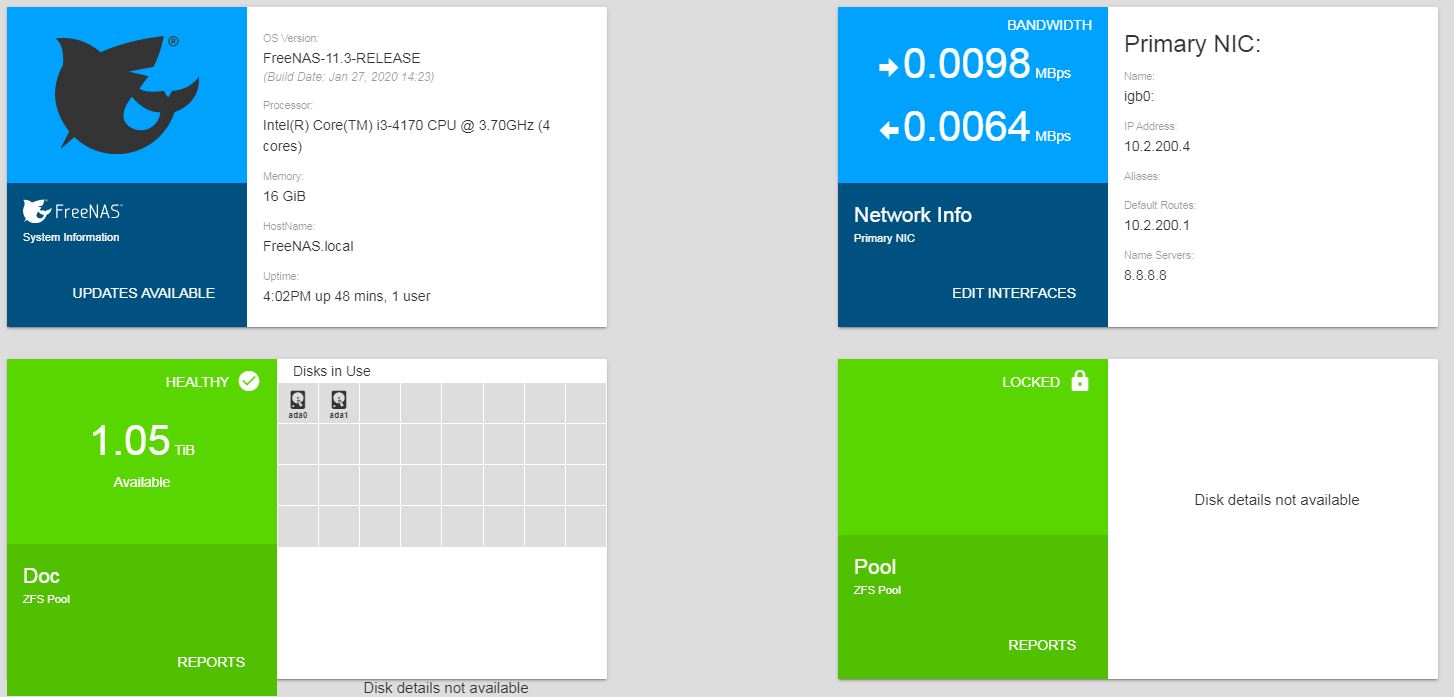
I then returned to 11.3-RELEASE and found the encrypted pool showing in the dashboard here as well. However, the dashboard did not look like the 11.3 - RELEASE it looks like this: ???
Next I tried suggested queries from another post on this forum. I admit I don't know what they do, but they did seem un-intrusive.
Finally,
First and foremost, whatever help I can get to unlock the encrypted pool WOULD BE GREATLY APPRECIATED. While I have tried to solve my FreeNAS problems on my own, this one is beyond my capabilities.
Lastly, what's with the 11.3-RELEASED desktop I have?
Thanks,
I next moved to another prior release (don't remember which one) where the encrypted pool was already showing in the dashboard (didn't need to be imported). Upon attempting to unlock it I got this error message:
Code:
Error: concurrent.futures.process._RemoteTraceback:
"""
Traceback (most recent call last):
File "/usr/local/lib/python3.7/concurrent/futures/process.py", line 239, in _process_worker
r = call_item.fn(*call_item.args, **call_item.kwargs)
File "/usr/local/lib/python3.7/site-packages/middlewared/worker.py", line 95, in main_worker
res = loop.run_until_complete(coro)
File "/usr/local/lib/python3.7/asyncio/base_events.py", line 579, in run_until_complete
return future.result()
File "/usr/local/lib/python3.7/site-packages/middlewared/worker.py", line 51, in _run
return await self._call(name, serviceobj, methodobj, params=args, job=job)
File "/usr/local/lib/python3.7/site-packages/middlewared/worker.py", line 43, in _call
return methodobj(*params)
File "/usr/local/lib/python3.7/site-packages/middlewared/worker.py", line 43, in _call
return methodobj(*params)
File "/usr/local/lib/python3.7/site-packages/middlewared/schema.py", line 964, in nf
return f(*args, **kwargs)
File "/usr/local/lib/python3.7/site-packages/middlewared/plugins/zfs.py", line 382, in import_pool
zfs.import_pool(found, found.name, options, any_host=any_host)
File "libzfs.pyx", line 369, in libzfs.ZFS.__exit__
File "/usr/local/lib/python3.7/site-packages/middlewared/plugins/zfs.py", line 380, in import_pool
raise CallError(f'Pool {name_or_guid} not found.', errno.ENOENT)
middlewared.service_exception.CallError: [ENOENT] Pool 17998721979278846804 not found.
"""
The above exception was the direct cause of the following exception:
Traceback (most recent call last):
File "/usr/local/lib/python3.7/site-packages/middlewared/plugins/pool.py", line 1656, in unlock
'cachefile': ZPOOL_CACHE_FILE,
File "/usr/local/lib/python3.7/site-packages/middlewared/main.py", line 1127, in call
app=app, pipes=pipes, job_on_progress_cb=job_on_progress_cb, io_thread=True,
File "/usr/local/lib/python3.7/site-packages/middlewared/main.py", line 1074, in _call
return await self._call_worker(name, *args)
File "/usr/local/lib/python3.7/site-packages/middlewared/main.py", line 1094, in _call_worker
return await self.run_in_proc(main_worker, name, args, job)
File "/usr/local/lib/python3.7/site-packages/middlewared/main.py", line 1029, in run_in_proc
return await self.run_in_executor(self.__procpool, method, *args, **kwargs)
File "/usr/local/lib/python3.7/site-packages/middlewared/main.py", line 1003, in run_in_executor
return await loop.run_in_executor(pool, functools.partial(method, *args, **kwargs))
middlewared.service_exception.CallError: [ENOENT] Pool 17998721979278846804 not found.
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/usr/local/lib/python3.7/site-packages/middlewared/job.py", line 349, in run
await self.future
File "/usr/local/lib/python3.7/site-packages/middlewared/job.py", line 386, in __run_body
rv = await self.method(*([self] + args))
File "/usr/local/lib/python3.7/site-packages/middlewared/schema.py", line 960, in nf
return await f(*args, **kwargs)
File "/usr/local/lib/python3.7/site-packages/middlewared/plugins/pool.py", line 1668, in unlock
raise CallError(msg)
middlewared.service_exception.CallError: [EFAULT] Pool could not be imported: 2 devices failed to decrypt.
I then returned to 11.3-RELEASE and found the encrypted pool showing in the dashboard here as well. However, the dashboard did not look like the 11.3 - RELEASE it looks like this: ???
Next I tried suggested queries from another post on this forum. I admit I don't know what they do, but they did seem un-intrusive.
Code:
root@FreeNAS:~ # grep -A 2 "geli attach" /var/log/*" Unmatched '"'.
Code:
root@FreeNAS:~ # sqlite3 /data/freenas-v1.db 'select vol_encryptkey from storage_volume where vol_name = "Pool";' 8ddf8b1e-faef-488b-80bf-7cab4485d271
Finally,
Code:
root@FreeNAS:~ # ls /data/geli 8ddf8b1e-faef-488b-80bf-7cab4485d271.key
First and foremost, whatever help I can get to unlock the encrypted pool WOULD BE GREATLY APPRECIATED. While I have tried to solve my FreeNAS problems on my own, this one is beyond my capabilities.
Lastly, what's with the 11.3-RELEASED desktop I have?
Thanks,
