Hi! I hope I'm at the right place with my question :)
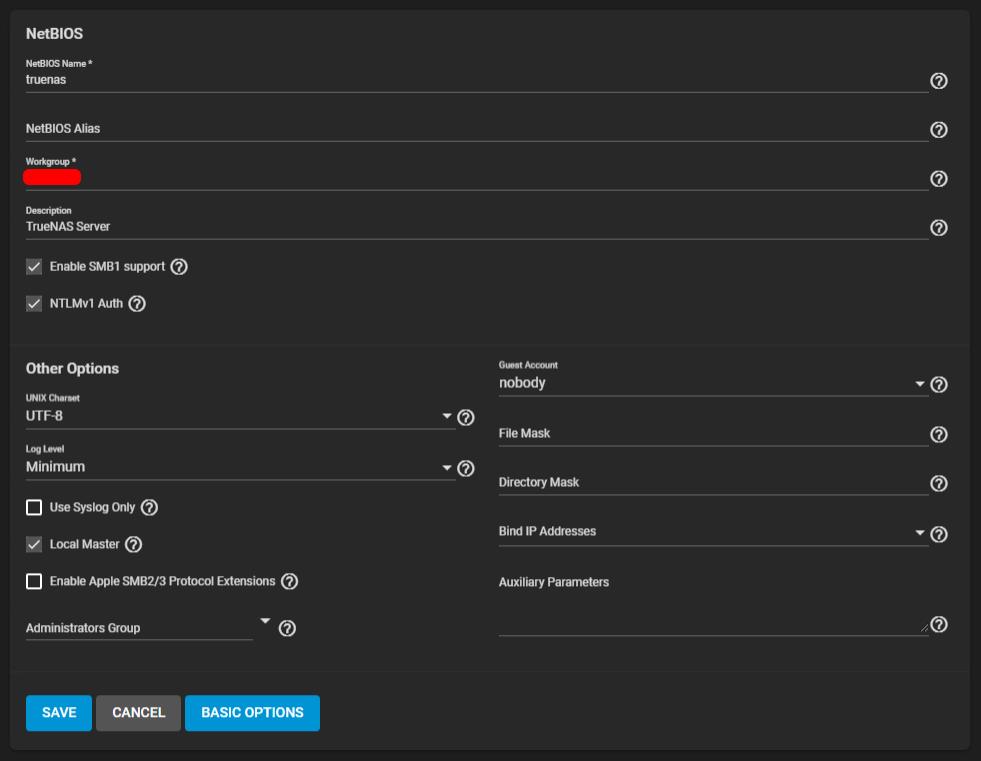
I was using FreeNAS-9.10.2-U6 without any issues and decided to upgrade TrueNAS-12.0-U7. We are using some old tech like multi function printers and embedded system which requires NTLMv1 authentication. On 9.10.2-U6 everything was working fine but on the new system I can't make it work. The nas is in Active Directory, and the "newer" machines are able to access the shares.
I checked the forum, set everything what I found but I'm still missing something. How can I make NTLMv1 working?
Here is my config:
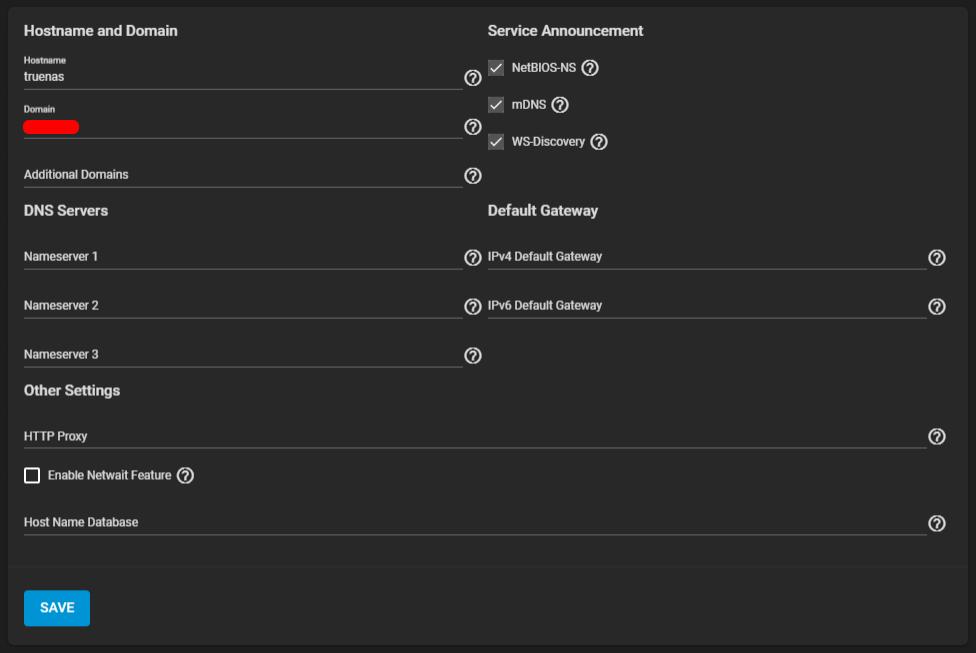
Network:
SMB:
Share:
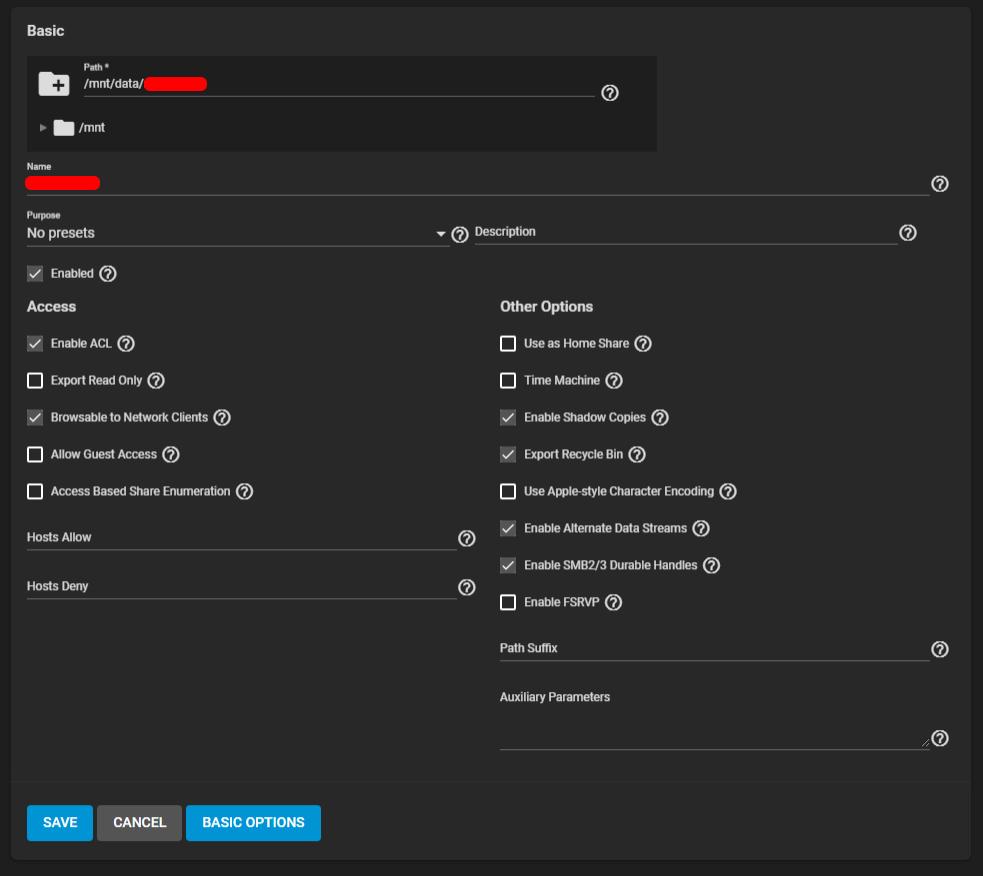
(I checked with "Allow Guest Access" and it didn't help)
testparm (I masked out sensitive parts with ******)
This is what I see in the logs when I try to access the server (I masked out sensitive parts with ******):
What is missing?
I was using FreeNAS-9.10.2-U6 without any issues and decided to upgrade TrueNAS-12.0-U7. We are using some old tech like multi function printers and embedded system which requires NTLMv1 authentication. On 9.10.2-U6 everything was working fine but on the new system I can't make it work. The nas is in Active Directory, and the "newer" machines are able to access the shares.
I checked the forum, set everything what I found but I'm still missing something. How can I make NTLMv1 working?
Here is my config:
Network:
SMB:
Share:
(I checked with "Allow Guest Access" and it didn't help)
testparm (I masked out sensitive parts with ******)
Code:
root@truenas[~]# testparm -s
Load smb config files from /usr/local/etc/smb4.conf
lpcfg_do_global_parameter: WARNING: The "client ntlmv2 auth" option is deprecated
Loaded services file OK.
Weak crypto is allowed
Server role: ROLE_DOMAIN_MEMBER
# Global parameters
[global]
aio max threads = 2
bind interfaces only = Yes
client ldap sasl wrapping = seal
client NTLMv2 auth = No
disable spoolss = Yes
dns proxy = No
domain master = No
enable web service discovery = Yes
kerberos method = secrets and keytab
kernel change notify = No
load printers = No
local master = No
logging = file
max log size = 5120
nsupdate command = /usr/local/bin/samba-nsupdate -g
ntlm auth = ntlmv1-permitted
preferred master = No
realm = ******.LOCAL
registry shares = Yes
restrict anonymous = 2
security = ADS
server min protocol = NT1
server role = member server
server string = TrueNAS Server
template shell = /bin/sh
winbind cache time = 7200
winbind enum groups = Yes
winbind enum users = Yes
winbind max domain connections = 10
workgroup = ******
idmap config *: range = 90000001-100000000
idmap config ******: range = 100000001-200000000
idmap config ******: backend = rid
idmap config * : backend = tdb
directory name cache size = 0
dos filemode = Yes
[******]
ea support = No
kernel share modes = No
path = /mnt/data/******
posix locking = No
read only = No
vfs objects = streams_xattr shadow_copy_zfs ixnas recycle crossrename aio_fbsd
recycle:subdir_mode = 0700
recycle:directory_mode = 0777
recycle:touch = yes
recycle:versions = yes
recycle:keeptree = yes
recycle:repository = .recycle/%D/%U
nfs4:chown = true
[******]
ea support = No
kernel share modes = No
path = /mnt/data/******
posix locking = No
read only = No
vfs objects = streams_xattr shadow_copy_zfs ixnas recycle crossrename aio_fbsd
recycle:subdir_mode = 0700
recycle:directory_mode = 0777
recycle:touch = yes
recycle:versions = yes
recycle:keeptree = yes
recycle:repository = .recycle/%D/%U
nfs4:chown = trueThis is what I see in the logs when I try to access the server (I masked out sensitive parts with ******):
Code:
{"timestamp": "2022-02-11T09:06:50.781216+0100", "type": "Authentication", "Authentication": {"version": {"major": 1, "minor": 2}, "eventId": 4625, "logonId": "0", "logonType": 3, "status": "NT_STATUS_WRONG_PASSWORD", "localAddress": "ipv4:10.0.1.2:445", "remoteAddress": "ipv4:10.0.1.25:37283", "serviceDescription": "SMB", "authDescription": null, "clientDomain": "*****", "clientAccount": "*****", "workstation": "10.0.1.25", "becameAccount": null, "becameDomain": null, "becameSid": null, "mappedAccount": "*****", "mappedDomain": "*****", "netlogonComputer": null, "netlogonTrustAccount": null, "netlogonNegotiateFlags": "0x00000000", "netlogonSecureChannelType": 0, "netlogonTrustAccountSid": null, "passwordType": "NTLMv1", "duration": 7128}}What is missing?
