broyuken
Cadet
- Joined
- Dec 20, 2023
- Messages
- 4
EDIT: I reinstalled TrueNas from scratch, imported my pools and AD worked fine. Not sure what the issue was but I worked around it.
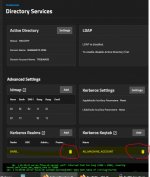
I upgraded my TrueNas core to Scale 23.10.1 the other day and now my SMB shares no longer work. I went into the active directory section and it shows AD and LDAP are both disabled. I try to re-enable it, but the username/password boxes do not show. How can I clear out the old AD settings to try to get this working once again?
I ran a bunch of commands I saw from previous posts but they didn't seem to match up and solve my issue.
I also tried running a command I found here on the forum which ended up erroring for me.
I upgraded my TrueNas core to Scale 23.10.1 the other day and now my SMB shares no longer work. I went into the active directory section and it shows AD and LDAP are both disabled. I try to re-enable it, but the username/password boxes do not show. How can I clear out the old AD settings to try to get this working once again?
I ran a bunch of commands I saw from previous posts but they didn't seem to match up and solve my issue.
Code:
root@broynas[~]# dig
; <<>> DiG 9.18.12-1-Debian <<>>
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37899
;; flags: qr rd ra; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;. IN NS
;; ANSWER SECTION:
. 86399 IN NS a.root-servers.net.
. 86399 IN NS b.root-servers.net.
. 86399 IN NS c.root-servers.net.
. 86399 IN NS d.root-servers.net.
. 86399 IN NS e.root-servers.net.
. 86399 IN NS f.root-servers.net.
. 86399 IN NS g.root-servers.net.
. 86399 IN NS h.root-servers.net.
. 86399 IN NS i.root-servers.net.
. 86399 IN NS j.root-servers.net.
. 86399 IN NS k.root-servers.net.
. 86399 IN NS l.root-servers.net.
. 86399 IN NS m.root-servers.net.
;; ADDITIONAL SECTION:
a.root-servers.net. 86399 IN A 198.41.0.4
;; Query time: 11 msec
;; SERVER: 10.0.86.203#53(10.0.86.203) (UDP)
;; WHEN: Wed Dec 20 16:35:04 EST 2023
;; MSG SIZE rcvd: 268
root@broynas[~]# host -t srv dc1.broyuken.com
dc1.broyuken.com has no SRV record
root@broynas[~]# host -t srv _ldap._tcp.broyuken.com
_ldap._tcp.broyuken.com has SRV record 0 100 389 dc1.broyuken.com.
_ldap._tcp.broyuken.com has SRV record 0 100 389 dc2.broyuken.com.
root@broynas[~]# 2023 Dec 20 16:56:50 broynas Device: /dev/sdd [SAT], 624 Currently unreadable (pending) sectors
2023 Dec 20 16:56:50 broynas Device: /dev/sdd [SAT], 624 Offline uncorrectable sectors
2023 Dec 20 16:56:51 broynas Device: /dev/sdd [SAT], 624 Currently unreadable (pending) sectors
2023 Dec 20 16:56:51 broynas Device: /dev/sdd [SAT], 624 Offline uncorrectable sectors
root@broynas[~]#
root@broynas[~]#
root@broynas[~]# midclt call kerberos.realm.query
[]
root@broynas[~]# klist
klist: No credentials cache found (filename: /tmp/krb5cc_0)
root@broynas[~]# ktutil list
ktutil:
ktutil: list
slot KVNO Principal
---- ---- ---------------------------------------------------------------------
ktutil: exit
root@broynas[~]# midclt call kerberos.keytab.query '[]' '{"count":true}'
0
root@broynas[~]#I also tried running a command I found here on the forum which ended up erroring for me.
Code:
root@broynas[~]# midclt call activedirectory.update '{"kerberos_principal": "", "enable": false}'
'bindpw'
Traceback (most recent call last):
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 201, in call_method
result = await self.middleware._call(message['method'], serviceobj, methodobj, params, app=self)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 1342, in _call
return await methodobj(*prepared_call.args)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/service/config_service.py", line 83, in update
rv = await self.middleware._call(
^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/main.py", line 1342, in _call
return await methodobj(*prepared_call.args)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 44, in nf
res = await f(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/schema/processor.py", line 177, in nf
return await func(*args, **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/middlewared/plugins/activedirectory.py", line 586, in do_update
elif not new['enable'] and new['bindpw']:
~~~^^^^^^^^^^
KeyError: 'bindpw'
root@broynas[~]#
Last edited: