Marc Lachapelle
Dabbler
- Joined
- May 22, 2022
- Messages
- 20
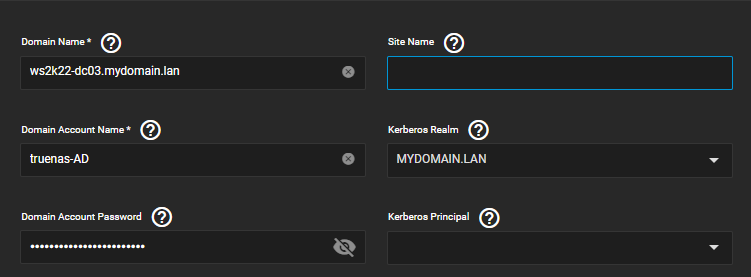
Hi, I was able to join my domain when I was using CORE. I currently use TrueNAS-SCALE-22.12.0. I have 3 redundant ADs, and they are on the same subnet as my TrueNAS SCALE. I can ping all my 3 ADs and
# host -t srv _ldap._tcp.mydomain.lan returns:
_ldap._tcp.mydomain.lan has SRV record 0 0 389 ws2k22-dc02.mydomain.lan.
_ldap._tcp.mydomain.lan has SRV record 0 0 389 ws2k22-dc01.mydomain.lan.
_ldap._tcp.mydomain.lan has SRV record 0 0 389 ws2k22-dc03.mydomain.lan.
# kinit truenas-AD@MYDOMAIN.LAN works properly
If I test using Samba
net ads lookup -S ws2k22-dc03.mydomain.lan returns:
Information for Domain Controller: 192.168.xxx.xxx
Response Type: LOGON_SAM_LOGON_RESPONSE_EX
GUID: 3b7c3080-3efb-42bf-b346-e50cca5432e9
Flags:
Is a PDC: yes
Is a GC of the forest: yes
Is an LDAP server: yes
Supports DS: yes
Is running a KDC: yes
Is running time services: yes
Is the closest DC: yes
Is writable: yes
Has a hardware clock: yes
Is a non-domain NC serviced by LDAP server: no
Is NT6 DC that has some secrets: no
Is NT6 DC that has all secrets: yes
Runs Active Directory Web Services: yes
Runs on Windows 2012 or later: yes
Forest: mydomain.lan
Domain: mydomain.lan
Domain Controller: ws2k22-dc03.mydomain.lan
Pre-Win2k Domain: MYDOMAIN
Pre-Win2k Hostname: WS2K22-DC03
Server Site Name: MySite
Client Site Name: MySite
NT Version: 5
LMNT Token: ffff
LM20 Token: ffff
# midclt call activedirectory.start
# midclt call core.get_jobs '[["method", "=", "activedirectory.start"]]' | jq returns
"error": "[EFAULT] kinit with password failed: kinit: Cannot find KDC for realm \"WS2K22-DC01.MYDOMAIN.LAN\" while getting initial credentials\n",
"exception": "Traceback (most recent call last):\n File \"/usr/lib/python3/dist-packages/middlewared/job.py\", line 426, in run\n await self.future\n File \"/usr/lib/python3/dist-packages/middlewared/job.py\", line 461, in __run_body\n rv = await self.method(*([self] + args))\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/activedirectory.py\", line 597, in start\n await self.middleware.call('kerberos.start')\n File \"/usr/lib/python3/dist-packages/middlewared/main.py\", line 1306, in call\n return await self._call(\n File \"/usr/lib/python3/dist-packages/middlewared/main.py\", line 1255, in _call\n return await methodobj(*prepared_call.args)\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/kerberos.py\", line 643, in start\n await asyncio.wait_for(self._kinit(), timeout=kinit_timeout)\n File \"/usr/lib/python3.9/asyncio/tasks.py\", line 481, in wait_for\n return fut.result()\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/kerberos.py\", line 442, in _kinit\n await self.do_kinit({'krb5_cred': cred})\n File \"/usr/lib/python3/dist-packages/middlewared/schema.py\", line 1284, in nf\n return await func(*args, **kwargs)\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/kerberos.py\", line 402, in do_kinit\n raise CallError(f\"kinit with password failed: {output[1].decode()}\")\nmiddlewared.service_exception.CallError: [EFAULT] kinit with password failed: kinit: Cannot find KDC for realm \"WS2K22-DC03.MYDOMAIN.LAN\" while getting initial credentials\n\n",
"exc_info": {
"repr": "CallError('kinit with password failed: kinit: Cannot find KDC for realm \"WS2K22-DC03.MYDOMAIN.LAN\" while getting initial credentials\\n')",
"type": "CallError",
"extra": null
},
Here is an extract from my /etc/krb5.conf
[domain_realm]
mydomain.lan = MYDOMAIN.LAN
.mydomain.lan = MYDOMAIN.LAN
MYDOMAIN.LAN = MYDOMAIN.LAN
.MYDOMAIN.LAN = MYDOMAIN.LAN
[realms]
MYDOMAIN.LAN = {
default_domain = MYDOMAIN.LAN
kdc = ws2k22-dc03.mydomain.lan
admin_server = ws2k22-dc03.mydomain.lan
kpasswd_server = ws2k22-dc03.mydomain.lan
}
What can I do next? Is it possible to use a procedure like Ubuntu manual AD join? , what would be the next step?
Thanks
# host -t srv _ldap._tcp.mydomain.lan returns:
_ldap._tcp.mydomain.lan has SRV record 0 0 389 ws2k22-dc02.mydomain.lan.
_ldap._tcp.mydomain.lan has SRV record 0 0 389 ws2k22-dc01.mydomain.lan.
_ldap._tcp.mydomain.lan has SRV record 0 0 389 ws2k22-dc03.mydomain.lan.
# kinit truenas-AD@MYDOMAIN.LAN works properly
If I test using Samba
net ads lookup -S ws2k22-dc03.mydomain.lan returns:
Information for Domain Controller: 192.168.xxx.xxx
Response Type: LOGON_SAM_LOGON_RESPONSE_EX
GUID: 3b7c3080-3efb-42bf-b346-e50cca5432e9
Flags:
Is a PDC: yes
Is a GC of the forest: yes
Is an LDAP server: yes
Supports DS: yes
Is running a KDC: yes
Is running time services: yes
Is the closest DC: yes
Is writable: yes
Has a hardware clock: yes
Is a non-domain NC serviced by LDAP server: no
Is NT6 DC that has some secrets: no
Is NT6 DC that has all secrets: yes
Runs Active Directory Web Services: yes
Runs on Windows 2012 or later: yes
Forest: mydomain.lan
Domain: mydomain.lan
Domain Controller: ws2k22-dc03.mydomain.lan
Pre-Win2k Domain: MYDOMAIN
Pre-Win2k Hostname: WS2K22-DC03
Server Site Name: MySite
Client Site Name: MySite
NT Version: 5
LMNT Token: ffff
LM20 Token: ffff
# midclt call activedirectory.start
# midclt call core.get_jobs '[["method", "=", "activedirectory.start"]]' | jq returns
"error": "[EFAULT] kinit with password failed: kinit: Cannot find KDC for realm \"WS2K22-DC01.MYDOMAIN.LAN\" while getting initial credentials\n",
"exception": "Traceback (most recent call last):\n File \"/usr/lib/python3/dist-packages/middlewared/job.py\", line 426, in run\n await self.future\n File \"/usr/lib/python3/dist-packages/middlewared/job.py\", line 461, in __run_body\n rv = await self.method(*([self] + args))\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/activedirectory.py\", line 597, in start\n await self.middleware.call('kerberos.start')\n File \"/usr/lib/python3/dist-packages/middlewared/main.py\", line 1306, in call\n return await self._call(\n File \"/usr/lib/python3/dist-packages/middlewared/main.py\", line 1255, in _call\n return await methodobj(*prepared_call.args)\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/kerberos.py\", line 643, in start\n await asyncio.wait_for(self._kinit(), timeout=kinit_timeout)\n File \"/usr/lib/python3.9/asyncio/tasks.py\", line 481, in wait_for\n return fut.result()\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/kerberos.py\", line 442, in _kinit\n await self.do_kinit({'krb5_cred': cred})\n File \"/usr/lib/python3/dist-packages/middlewared/schema.py\", line 1284, in nf\n return await func(*args, **kwargs)\n File \"/usr/lib/python3/dist-packages/middlewared/plugins/kerberos.py\", line 402, in do_kinit\n raise CallError(f\"kinit with password failed: {output[1].decode()}\")\nmiddlewared.service_exception.CallError: [EFAULT] kinit with password failed: kinit: Cannot find KDC for realm \"WS2K22-DC03.MYDOMAIN.LAN\" while getting initial credentials\n\n",
"exc_info": {
"repr": "CallError('kinit with password failed: kinit: Cannot find KDC for realm \"WS2K22-DC03.MYDOMAIN.LAN\" while getting initial credentials\\n')",
"type": "CallError",
"extra": null
},
Here is an extract from my /etc/krb5.conf
[domain_realm]
mydomain.lan = MYDOMAIN.LAN
.mydomain.lan = MYDOMAIN.LAN
MYDOMAIN.LAN = MYDOMAIN.LAN
.MYDOMAIN.LAN = MYDOMAIN.LAN
[realms]
MYDOMAIN.LAN = {
default_domain = MYDOMAIN.LAN
kdc = ws2k22-dc03.mydomain.lan
admin_server = ws2k22-dc03.mydomain.lan
kpasswd_server = ws2k22-dc03.mydomain.lan
}
What can I do next? Is it possible to use a procedure like Ubuntu manual AD join? , what would be the next step?
Thanks

