Hey guys,
I have a working setup right now where I have my home drives accessible on Linux and Windows through AD. Lately, I had a minor issue and I was wondering how best to tackle it. According to my current mode for my 'User' storage I have it set as
Now, this isn't really a problem at first because Linux understands my ACLs and the permissions work perfectly. However, I had an issue where some tasks in Linux are not a fan of seeing the
This made sense to me but the permissions do not take effect. Is this due to the "Apply Mode" being checked? I don't really want to start screwing with something I do not know enough about. My goal is to get that
I have a working setup right now where I have my home drives accessible on Linux and Windows through AD. Lately, I had a minor issue and I was wondering how best to tackle it. According to my current mode for my 'User' storage I have it set as
070 (---rwx---) this is of course greyed out in FreeNAS since this is a Windows share not a Unix share.Now, this isn't really a problem at first because Linux understands my ACLs and the permissions work perfectly. However, I had an issue where some tasks in Linux are not a fan of seeing the
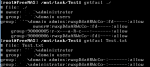
070 and that the file is not owned by the current user. My though was simple, let's just add uid=${UID},forceuid and set it to the proper user since my ACLs will still govern the files. Great, but what about the 070 permissions? So I thought I'd add 4 lines to the end of my share:Code:
inherit acls = yes inherit owner = yes acl group control = yes access based share enum = yes create mask = 0777 force create mode = 0600 directory mask = 0777 force directory mode = 0700
This made sense to me but the permissions do not take effect. Is this due to the "Apply Mode" being checked? I don't really want to start screwing with something I do not know enough about. My goal is to get that
070 to read 600 for the files in my home directory share without disrupting my ACLs. Thanks!
Last edited: