Kindly note that I have spent countless DAYS trying to get Nextcloud up and running, and as a last resort I'm asking for the counsel of the FreeNAS community. I know there are a number of moving parts, including pfSense, so this may not be the most appropriate place to post this plea for help. I need help tying everything together as this is driving me insane. In an attempt to assist, I've tried to clearly define my Objective, Configuration, Constraints, as well as pfSense Config.
Any help that can be offer would truly be appreciated!
Objective:
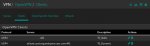
[1] pfSense: VPN / OpenVPN / Clients
Summary:
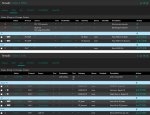
TG_DYNAMIC Config:



TG_STATIC Config:



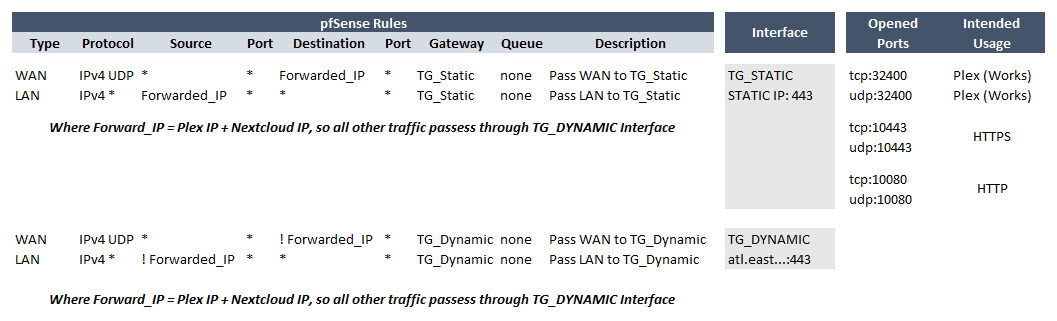
[2] pfSense: Firewall / Rules / WAN & LAN
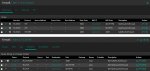
[3] pfSense: Firewall / NAT / Port Forward
Any help that can be offer would truly be appreciated!
Objective:
- Deploy Nextcloud 12, hardened, and accessible at domain: DOMAIN.com
- I don't care how I get there, whether jail, Ubuntu VM, etc.
- I have two issues: (a) I can't connect the internal Nextcloud IP to DOMAIN.com and (b) I can't use certbot to obtain SSL
- VMware ESXi 6.5.0 Update 1
- FreeNAS-11.0-U4
- pfSense 2.4.2-RELEASE
- DOMAIN.com redirected to TG_STATIC IP
- Double NAT scenario with no static IP offered by ISP.
- Ports which can't be opened by VPN provider: Code:
tcp:4500,udp:4500,tcp:6060,udp:6060,tcp:4443,udp:4443,tcp:7070,udp:7070,tcp:8443,udp:8443,tcp:8444,udp:8444,tcp:8445,udp:8445,tcp:8446,udp:8446,tcp:8447,udp:8447,tcp:8448,udp:8448,tcp:8449,udp:8449,tcp:8450,udp:8450,tcp:8451,udp:8451,tcp:8452,udp:8452
- While I don't care much about Plex being externally accessible, I used that as a "test case" to defeat the fact that I'm being double NATed and don't have a static IP.
- I did so with the following configuration in pfSense: (a) Configured OpenVPN Clients [1], (b) Created appropriate Firewall Rules [2], (c) and Added a Port Forward [3].
- Plex is externally accessible. Shamefully I should admit this took me quite some time to figure out.
[1] pfSense: VPN / OpenVPN / Clients
Summary:
TG_DYNAMIC Config:



TG_STATIC Config:



[2] pfSense: Firewall / Rules / WAN & LAN

[3] pfSense: Firewall / NAT / Port Forward


