Hi all, I have been using my freenas for over a year. It has been working fine however the first symptom that I realize is my nextcloud starts showing 523 origin is unreachable. DNS by cloudflare. I have verified that the IP is right however it just can't reach to my server. I did a restart to the server and it starts working again.
But in these 2 days, reaching NAS at home network is unreasonable slow. And easy to show errors when copying files. These symptoms have never happen before.
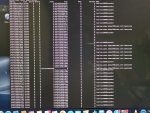
I also checked with netstat and found the image attached below. (192.168.2.142 is my iMac's IP address). Is this DDoS attack? What should I do next?
Many thanks,
twsps
But in these 2 days, reaching NAS at home network is unreasonable slow. And easy to show errors when copying files. These symptoms have never happen before.
I also checked with netstat and found the image attached below. (192.168.2.142 is my iMac's IP address). Is this DDoS attack? What should I do next?
Many thanks,
twsps