
How to Set Up and Install TrueNAS CORE
In this tutorial, we’re going to walk you through the basic requirements to run the TrueNAS storage operating system, from creating the installation media and installing it onto your system.

TrueNAS CORE 13.3 Plans
Where Open Storage Began TrueNAS has come a long way and has delivered incalculable value to millions of users around the world. After nearly 20 years of evolution since its inception in 2005 as FreeNAS, TrueNAS CORE has proven to be the most reliable and...
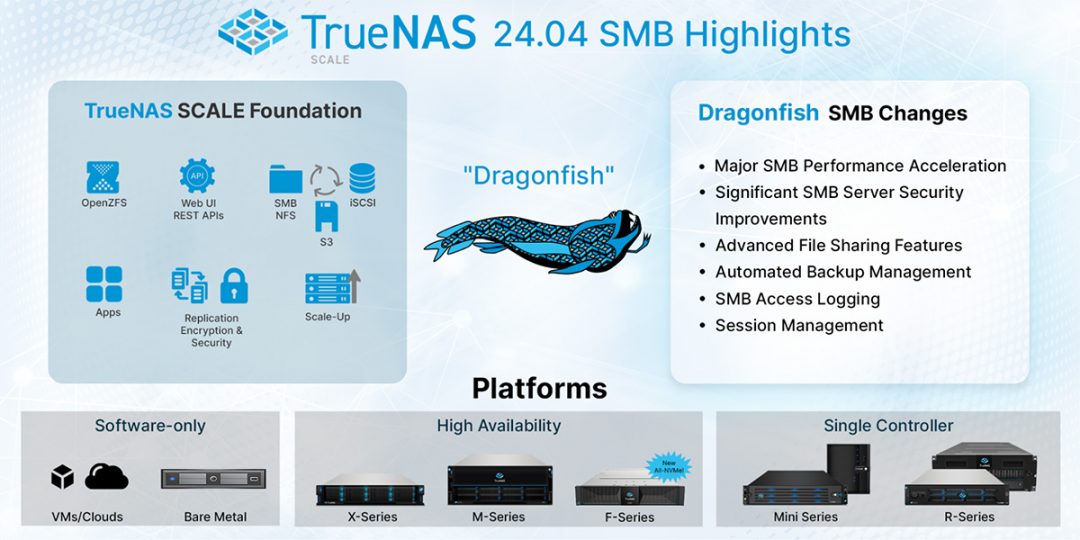
TrueNAS SCALE Dragonfish improves SMB Services and Performance
The Dragonfish chapter of TrueNAS SCALE moves to the second stage with the release of TrueNAS SCALE 24.04-RC1. After a successful BETA release with thousands of users, it's time for some serious testing of the Release Candidate that is now available. TrueNAS SCALE...
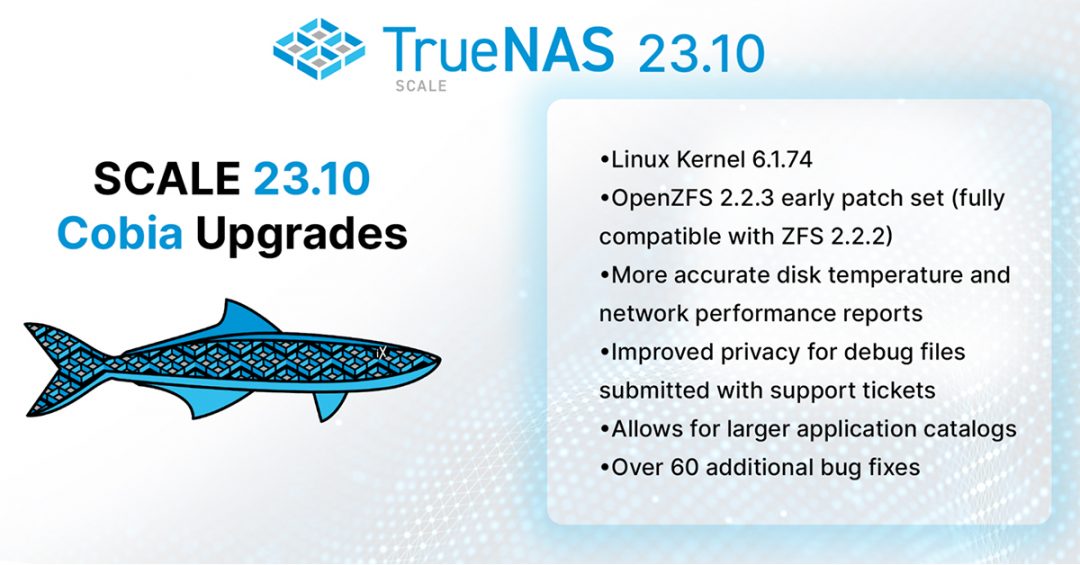
TrueNAS SCALE 23.10.2 delivers Enterprise Quality
TrueNAS SCALE 23.10 “Cobia” was released in October 2023 and has been deployed over 60,000 times since then, setting a new record for TrueNAS adoption rate. To date, TrueNAS SCALE is running on over 105,000 systems with over 2,000 petabytes of storage managed. On...

TrueNAS Enterprise Again Named a Gartner Peer Insights™ Customers’ Choice for Primary Storage in 2024
Thank You iX Customers! We are honored to share that for the second consecutive year, iXsystems and our product TrueNAS Enterprise have been named a North America Customers' Choice in the Gartner Peer Insights™ Voice of the Customer Report for Primary Storage. This...

Beyond VMware: Exploring Virtualization Alternatives
There is a growing demand among individuals, businesses, and organizations for alternative virtualization solutions, especially given the drastic shift in strategy and resulting price increases for VMware following its acquisition by Broadcom. We surveyed the VMware...

Fast Dedup is a Valentines Gift to the OpenZFS and TrueNAS Communities
With much love for the communities, iXsystems and Klara have developed and donated the Fast Dedup capability for OpenZFS. The Open Source software has been made available to the OpenZFS community for review, further testing and integration into a future release of...

TrueNAS SCALE Dragonfish Reaches BETA
The Dragonfish chapter of TrueNAS SCALE has begun. Building on its foundation of high availability, scale-up storage, and easy deployment of containerized applications, TrueNAS SCALE is now poised to expand its capabilities even further. Today, we announce the...

Why Traditional Enterprise Storage is So Expensive
Traditional storage vendors are large public corporations whose foremost obligation is to deliver shareholder value. Through a proprietary, closed-source approach born decades ago, they promote a mindset of scarcity and create environments that lock customers into...

How TrueNAS Delivers Unbeatable Value
What We Do At iXsystems, we do not answer to the same Wall Street or Venture Capital stakeholders that other vendors do. This allows us to focus exclusively on making our customers successful, powered by our core value to always “think people before profit”. The...